Search Results for "end user security awareness"
Find videos related to your search query. Browse through our collection of videos matching "end user security awareness". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "end user security awareness"
50 results found

3:01
What is SECURITY AWARENESS? What does SECURITY AWARENESS mean? SECURITY AWARENESS meaning
tophoto
1 views
![[HKITF] Cyber Security Conference 2014 - Security of End User-based Cloud Services](/image/i.ytimg.com/vi/_PmuDU6r_lY/hqdefault.jpg)
21:31
[HKITF] Cyber Security Conference 2014 - Security of End User-based Cloud Services
HKITF 01
22 views

1:44
End to end encryption meaning in Hindi | End to end encryption ka matlab kya hota hai
Worldwide Spoken English By VS
130.1K views
3:34
Instagram end-to-end encryption kya hai | End To End Encryption turn on Chats |Instagram New Update
Upcoming World
46.4K views
0:29
How to Turn Off End to End Encryption in Messenger 2024 | Remove End to End Encryption on Messenger
Tech Babo Vai
444.4K views
3:39
End to End Encryption Sinhala | End to End Encrypted WhatsApp and Messenger | How It's Works Chat
Hiruuu Tech
5.2K views
0:55
(New) Turn off End to end encrypted on messenger | Turn off end-to-end encrypted (2025) #endtoend
Solution Prove
173.9K views
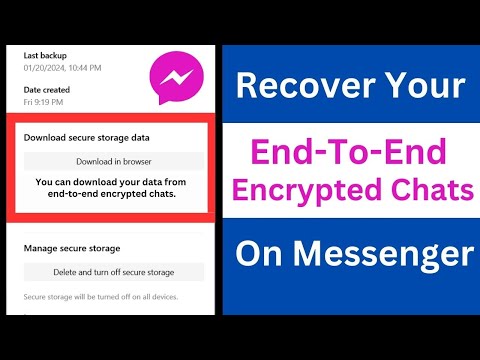
1:42
How to Recover End-To-End Encrypted Chats on Messenger | Restore End-To-End Encrypted Chats
World 360
369.3K views

8:58
WhatsApp ~ এর End to End Encryption কি এবং এর কাজ কি || How To Use End to End Encrypted Backup
TecH Bangla Info
3 views
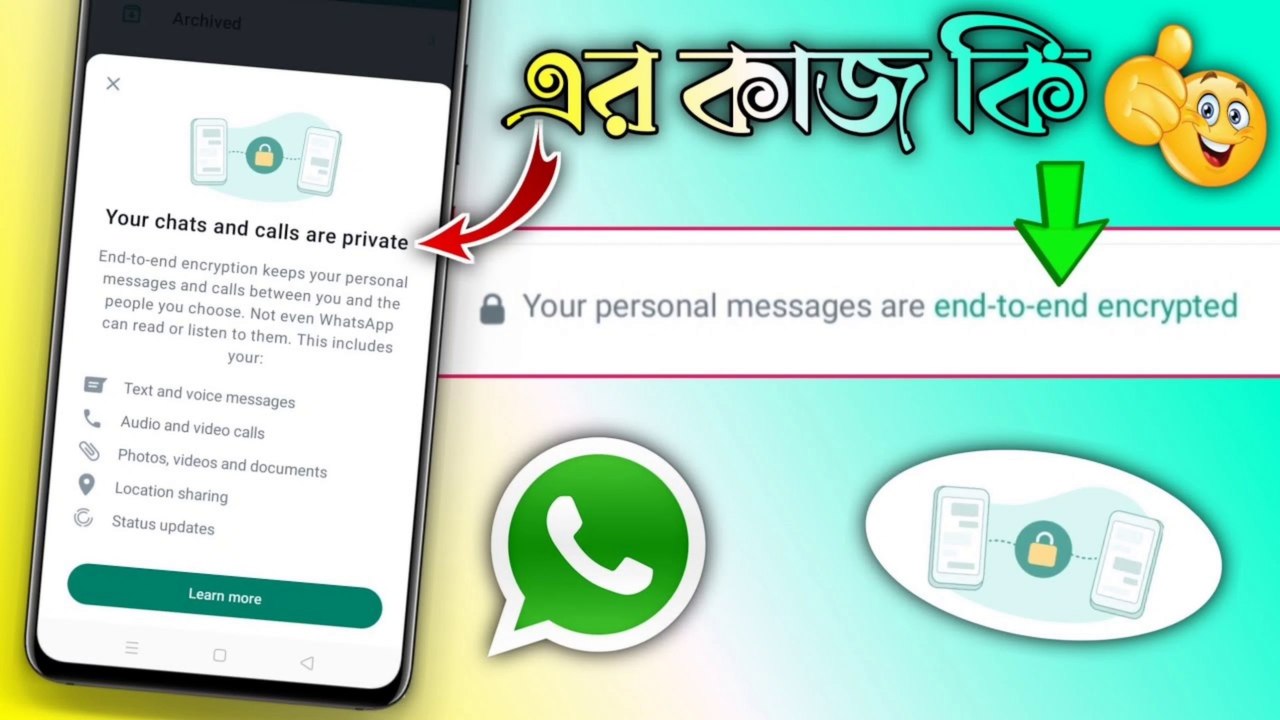
3:32
WhatsApp ~ এর End to End Encrypted এর কাজ কি || How to Use Whatsapp End to End Encryption
TecH Bangla Info
10 views

17:57
Mental Health Awareness Month: Raising awareness on men's mental health
Guardian Nigeria
766 views

0:21
IRCTC User Id & password kaise banaye Hindi #How to create IRCTC user is & password
BIKASH 4888
3.1M views

14:01
VB.NET Creating Login with Admin & User (User Level)
Codinger Tutorial
14 views

8:22
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
8 views

5:39
How to input data from keyboard in python | keyboard input in python | read data from keyboard | python practically | easy way of python programming | python basics | read data from user | input from user in python | input function in python
ALL IN ONE
1 views
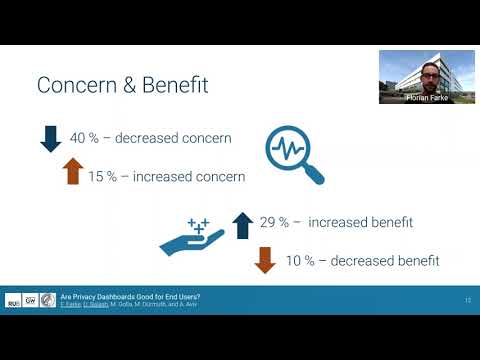
12:32
USENIX Security '21 - Are Privacy Dashboards Good for End Users? Evaluating User Perceptions...
USENIX
162 views
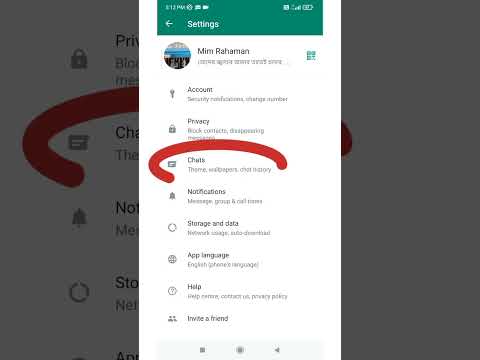
0:15
END-TO-END ENCRYPTION..saathi..security by Default. whatsapp security..
Majmua khatun
3.0M views

2:04
Talent Development Support - Travellers Security Awareness - TDS Digital Security
Tb
1 views

1:02:42
Power BI Project From Start to End Part 2 | Car Sales | Advanced DAX | End to End |2024 #powerbi
Data Tutorials
45.0K views

10:46
End Portal की खोज | Minecraft End Portal Kaise Banaen | End Portal Minecraft PE
Khempur Games
4 views

1:48:09
Unfair: The End - アンフェア the end - Anfea the end
SlipatuLociza
9.3K views

8:31
All THE END BRAINROT Animals but They All Normal | This is THE END BRAINROT THE END #quizgalaxy
quizgalaxy410
3.0K views

1:07:11
Power BI Project From Start to End Part 1 | Car Sales | Advanced DAX | End to End |2024 #powerbi
Data Tutorials
95.4K views

11:34
Advantage of Cryptography Tools & Securing End User Equipment
Ziauddin Zia
40 views
![[EN] end-user experience is key, especially for networks part 1 [video]](/image/s2.dmcdn.net/v/3hW1M1eBPo9269Y4a/x720)
1:41
[EN] end-user experience is key, especially for networks part 1 [video]
Orange Business Services
141 views

0:26
Read Computational Advancements in End-user Technologies: Emerging Models and Frameworks (Advances
Esme Moss
0 views

0:57
End-to-End Encryption Explained in a Minute | Data Encryption | Data Privacy and Security | #shorts
SCALER
23.7K views

0:54
What is End to End Encryption cyber security terminology#vlrtraining #cybersecurity #education
VLR Training
131 views
0:33
End-to-End Encryption (E2EE) Explained #security #cryptography
ByteQuest
4.5K views

5:18
WhatsApp Security Updates - End-to-End Encryption Full Details - Verify Your Contact
Sujon5
7 views

5:16
Whatsapp Security End-To-End Encryption Not Secure ! Detail Explained
TechInfoEdu
1 views
4:40
Whatsapp End to End Encryption | Good or Bad? Best in Security?
Kisudonozo
6 views

12:37
How End-to-End Encryption works | The Signal Protocol and Privacy Vs Security
Harshit Rautela
12.3K views

32:58
End-to-end encryption, code security & JavaScript cryptography
MEGA
39.6K views
0:48
Botnet | Info | Cybersecurity | Security Awareness | Karthik SR
Karthik SR Kcyber
189 views

0:16
What is IDS | Intrusion Detection Systems | Info | Cybersecurity | Security Awareness| Karthik SR
Karthik SR Kcyber
9.0K views

0:15
what is SECURITY AWARENESS TRAINING #Cybersecurity #TechEducation #onlinelearning #definitions
Keerthan V Suvarna
13 views

1:31
Cyber Security Awareness
Instavid
1 views

11:22
Cyber Security Awareness Seminar in Ahmedabad
Gujarat Headline
8 views

8:01
Web Security-Security Threats and their solution in hindi-Security Policy-computer network security
Unbeaten Learning
77.8K views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

19:53
User authentication protocols | Cryptography and System Security
Ekeeda
307 views
12:25
Visual Cryptography with Cloud Computing for Personal Security of the User
IJERT
12 views
4:58
Distributed Programming Fullstack 2021 | S3P42 | Security | Add Create User Form and Call Backend
Lars Bilde
249 views

13:49
Remote User Authentication using Asymmetric Encryption in Network Security | Woo and Lam Proposal
Chirag Bhalodia
30.0K views

7:13
Data Integrity & Information Security in Windows - User Accounts + NTFS Permissions
Samuel Nadeau
12 views
1:20
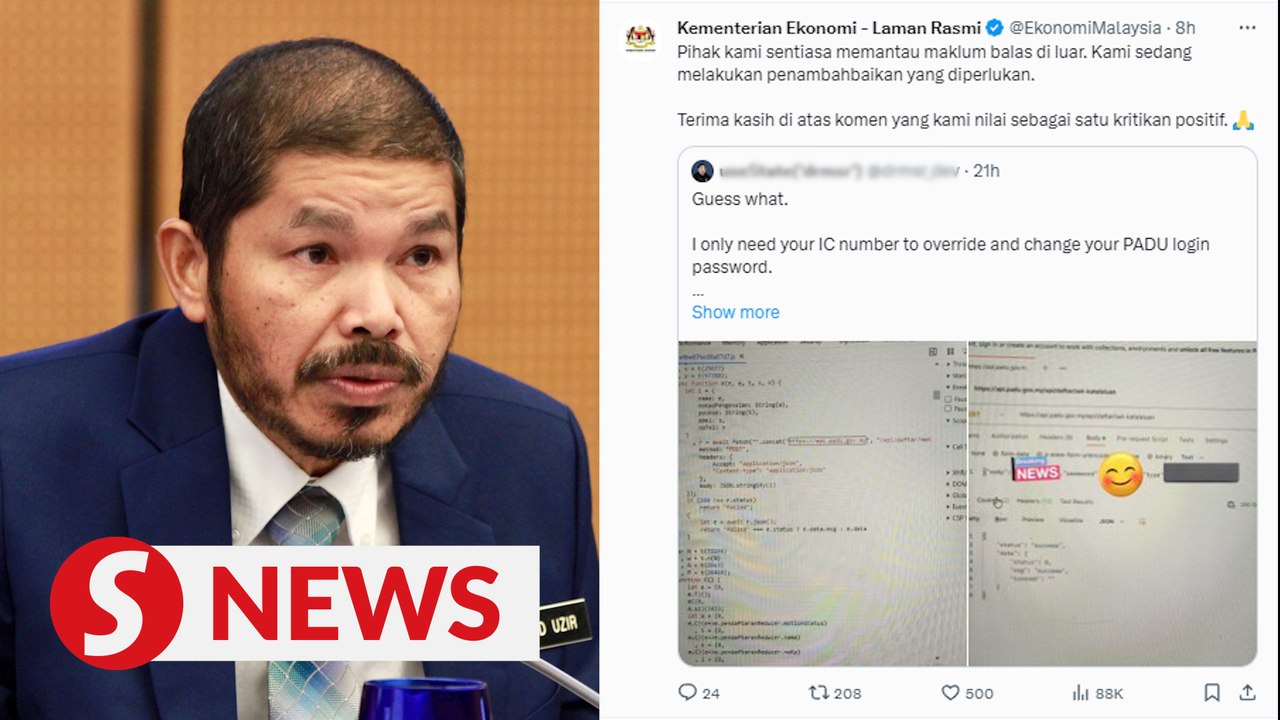
Economy Ministry swiftly fixes security loophole in Padu, thanks user for highlighting issue
The Star
2.5K views

5:23:58
End to end Deep Learning Project Implementation using MLOps Tool MLflow & DVC with CICD Deployment 🚀
DSwithBappy
83.8K views

0:57
Unlock The Secret: Disabling End-to-end Encryption On Messenger
The IdioTech TV
316.7K views

22:17
Oral Session: End-To-End Memory Networks
Microsoft Research
3.2K views
Page 1