Search Results for "and SHA-512"
Find videos related to your search query. Browse through our collection of videos matching "and SHA-512". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "and SHA-512"
50 results found

1:39
SHA Happy Birthday Song – Happy Birthday SHA - Happy Birthday Song - SHA birthday song #SHA
Greetings with name
223 views

11:42
SHA 1 | Secure Hash Algorithm | Working of SHA 1 | Parameters of SHA512 and SHA 256
Chirag Bhalodia
73.4K views

14:50
SHA 256 | SHA 256 Algorithm Explanation | How SHA 256 Algorithm Works | Cryptography | Simplilearn
Simplilearn
179.4K views

10:16
SHA – Secure Hash Algorithm in Hindi - Properties, Working, Comparison b/w SHA and MD5
Easy Engineering Classes
196.1K views
12:16
How Does SHA-1 Work - Intro to Cryptographic Hash Functions and SHA-1
Fullstack Academy
69.1K views

0:57
Understanding SHA-1 & SHA-256 Hash Functions Explained
TWiT Tech Podcast Network
7.8K views

0:29
World of Warcraft Patch 5.4: Sha of Pride (Sha de l'Orgueil)
JudgeHype
211 views
0:56
How to Get SHA1 or SHA-256 key in Android Studio for firebase Flutter | Easy & First Tricks. Sha-1 Key Terminal Flutter.
Instructive Tech
5 views
6:09
cryptography and network security sha 3 keccak and ripemd 160
CodeMade
14 views

37:17
How we created the first SHA-1 collision and what it means for hash security - Defcon 25
Elie Bursztein
9.2K views

10:03
Cryptography Hashing functions SHA and specificaly SHA1 hashing
Alon Lalezari - אלון ללזרי
11 views

4:20
SHA function in Cryptography and cyber security tamil||CCS||Anna university reg-2021.
Murugan Tech World
5.5K views
10:54
Secure Hash Algorithm (SHA) in Cryptography and Network Security #cryptography #networking #security
Lab Mug
11.2K views

0:40
Unlocking cryptography to secure your data. AES,RSA,SHA, and MD5
MossB Network
167 views

1:54
What is a Bitcoin hash and SHA-256
99Bitcoins
25.0K views
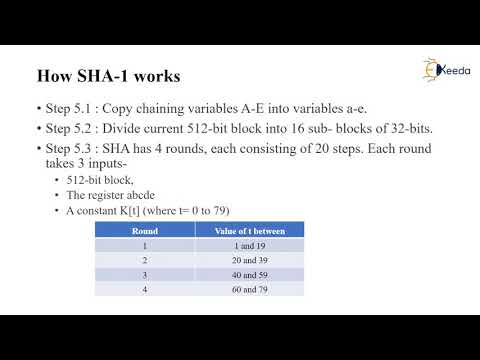
17:51
SHA 1 | Cryptography and Network Security
Ekeeda
2.7K views

49:40
Top Hashing Algorithms In Cryptography | MD5 and SHA 256 Algorithms Explained | Simplilearn
Simplilearn
21.5K views

10:50
Secure Image Storage Application with Owner Alerts using AES and SHA-256 | SUBJECT: CSA33303
Adam Mirza
98 views

55:46
Secure Hash Algorithm (SHA): A Comprehensive Analysis-Foundations, Evolution, Applications, and P...
Hello InfoSec
16 views

56:42
Cryptanalysis of AES and SHA-2: how far we are from compromising worldwide encryption
Microsoft Research
971 views

5:11
2. Hash Function and its properties | SHA-256 - Cryptography series
InvolveInInnovation
1.2K views

13:29
AES and SHA Cryptography Library for Chisel
Chisel
396 views

10:06
SHA-256 Simplified: What Is It And Why It Is So Secure
The Bitcoin Express
32.4K views
![What is a Bitcoin hash and SHA-256 [HD, 720p]](/image/s2.dmcdn.net/v/GS2U01cmKFkEYQqDj/x720)
1:54
What is a Bitcoin hash and SHA-256 [HD, 720p]
Vijay Sai
5 views

7:03
A Tale of Two Athletes: Gwen Berry and Sha'Carri Richardson
Styxhexenhammer666
360 views

2:13
IOC Says Sha'carri Richardson and Kamila Valieva's Doping Controversies Are 'Very Different'
People
801 views

0:15
Unlocking the Power of Proof of Work and SHA-256
Crypto X
685 views
0:46
A Multiple-Medical-Image Encryption Method Based on SHA-256 and DNA Encoding | RTCL.TV
STEM RTCL TV
52 views

28:17
Parte 1 - Introdução ao Algoritmo SHA 256 - Secure Hash Algorithm SHA256
Laboratório de Inutilidade Pública
7.2K views

25:20
Asymmetric Key Cryptography & Hashing Explained | RSA, DSA, SHA-256 in Blockchain Part 03 Hindi 2025
Akshay Kurhekar
116 views

0:35
Cracking The Code - Exploring Secure Hash Algorithms - SHA Short #cybersecurity #hashing
Technically U
1.1K views

6:17
Bitcoin & SHA-256 Explained With Animations
I Explain Crypto
1.1K views

28:38
#ክሪፕቶግራፊ How Blockchain Uses SHA-256 for Cryptographic Hashing | Simplified in Amharic
Self Programmers
268 views

17:40
AES RSA PGP GPG SHA - Qu'est-ce que c'est ?
Paf LeGeek
34.0K views
1:00
Exploring Cryptography: SHA-256 to Blake3 Transition
Stephen Blum
264 views
0:37
How SHA 3 processes cryptographic data with just 2
Cyber Freedom 2025
742 views

6:39
Hash-Funktionen: SHA &Co. // deutsch
the native web GmbH
8.0K views
0:14
Sha'Carri Richardson American Athlete #shorts
Strong Mind Set
143.7M views

32:34
SHA-256 (COMPLETE CONCEPT & DETAILED STEP-BY-STEP EXPLANATION)
Xiuminseokie21
21.7K views

0:57
SHA-256: The Ultimate Weapon Against Hackers – Here’s Why! #sha256 #cybersecurity #programming
Code
2.2K views

2:14
Bitcoin Security Explained: The Role of SHA-256 #sha256 #bitcoin #cryptocurrency
Cryptocurrency Guide
39 views
4:57
Explication de SHA-256 🔑 Blockchain : enjeux et mécanismes cryptographiques
MOOC de l'IMT
5.3K views

0:25
CyberSecurity Definitions | Secure Hash Algorithm (SHA)
Relative Security
3.2K views

2:44
What Is The SHA Family? - SecurityFirstCorp.com
SecurityFirstCorp
16 views

0:46
Unlocking SHA-256: The Hunt for the Special Number
Tech Chips
10.8K views
10:21
SHA: Secure Hashing Algorithm - Computerphile
Computerphile
1.3M views

3:24
Kala Sha Kala - Full | OM | Aditya Roy K, Elnaaz , Sanjana S | Enbee,Amjad Nadeem,Raahi,Dev N,Kumaar
Zee Music Company
80.0M views
22:59
How Does SHA-256 Work?
learnmeabitcoin
362.6K views

11:03
Learn the ART of CRYPTOGRAPHY - SHA-1 HMAC Hashing Explained (Urdu/Hindi)
Cybersecurity Academy - CertificationHUB
184 views

12:48
Função de Hash - MD5 e SHA - Código HMAC - Aula completa
Prof. Sergio Villarreal
3.7K views