Search Results for "Secure Keys"
Find videos related to your search query. Browse through our collection of videos matching "Secure Keys". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Secure Keys"
50 results found

1:05
X-keys USB Stick Keys with 16 programmable keys Review
Ardellaii
26 views

23:53
(Mario) The Music Box part 3 - Keys keys keys...
RobBoberty
2 views

7:15
How to secure Gmail ? || Gmail ko secure kaise kare ?क्या आपका Gmail Secure है ?
DoWithMe Start Learning
1 views

11:38
Podcast Kryptographie: Juggerknaut Schlüssel Keys (deutsch, Juggerli Keys, Zero Knowledge)
Spot-On Encryption Suite Messenger
3 views

3:49
Was sind Public Keys, Private Keys und Wallet Adressen? | Lesson 7 Bitpanda Academy
Bitpanda
2.7K views

11:10
Cryptography keys...|| Symmetric vs Asymmetric keys.... details... concepts..... part 03..
TechnologyHome tuition
38 views

0:51
Public Keys vs Private Keys 🔑 Crypto Wallets Explained! 🚀 (In 50 Seconds! 👍) #cryptocurrency
Crypto Casey
11.3K views

0:59
Public Keys vs. Symmetric Keys: Security for Everyone, Everywhere
Zcash Media
1.0K views

4:50
Web 3 Tech Series - Public Key Cryptography - What are secret keys and public keys?
Hubel Labs
116 views

7:30
Quick Look: Two Keys Are Better than One but Three Keys Are Better than Two
RSA Conference
808 views

7:24
Symmetric Keys, Asymmetric Keys, Public Key Encryption And Man In The Middle Attack
Akshay N
18 views

46:32
Two Keys Are Better than One but Three Keys Are Better than Two
RSA Conference
146 views

7:31
Private Keys & Public Keys: Grundlagen der Kryptographie & Sicherheit im Bitcoin-Netzwerk | 005
BTC Vision
15 views

3:32
Public and Private Keys - Public Key Cryptography - SSH Keys - Public Key RSA Encryption Decryption
Cloud Concepts
48 views

3:53
Signing using asymmetric keys | Public & Private Keys and Digital Signatures |Network Security
Software Systems
580 views

10:22
Foundation of Distributed Systems Security | Symmetric Keys | Asymmetric Keys | Digital Certificates
Think Software
3.4K views

0:48
What are Public Keys & Private Keys in #Crypto #cryptowallet
Sahicoin
9.0K views
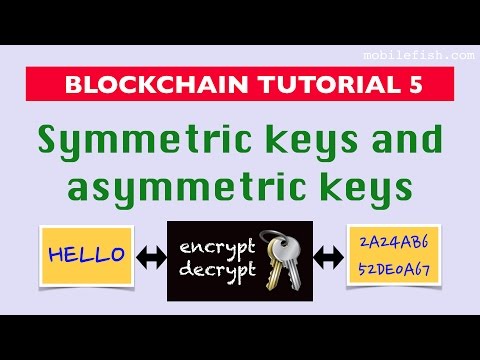
6:30
Blockchain tutorial 5: Symmetric keys and asymmetric keys
Mobilefish.com
14.8K views

5:15
How Crypto wallets work | 🗝🔐Private keys & Public Keys | Private aur Public key kya hai | Hindi/Urdu
Haroon VOICE
816 views

1:00
What are Keys in Blockchain? | Public Key and Private Key | Crypto Keys? | Describedot | Day 11
Describedot
9.1K views

0:32
Auto locksmith, car locksmith, car key, car keys, lost car keys
Zoey Smith
1 views

0:56
X-keys USB Professional (58 Keys)
Samageurnrayani
20 views

1:03
CaviarDream - Keys and Keys
CaviarDream
2 views

1:01
shortcut keys of android studio for android app developement and for more thing you can use this shortcut keys,helpful
C#,Wordpress& Android tutorial project review
1 views

1:38
How To Use MS Office With Short Keys - Basic Training Of Ms Office Short Keys - 17 Special Short Cuts Of MS Office
Josh 2000
35 views

1:37
Top 10 coolest Supercar touch Keys ¦ Concept keys of Sports Car-トップ10のクールなスーパーカーのタッチキー ¦ スポーツカーのコンセプトキー
Linh nguyen
9 views

6:50
keyboard keys details | keyboard keys explanation in hindi
Technical kamranji
6 views
10:00
How to download title keys & prod keys for yuzu | Animal Crossing New Horizons
Solid Guides
370 views

9:12
How to download title keys & prod keys for yuzu | Pokémon Brilliant Diamond
Imperius Clutch
401 views
0:06
Ms Excel shortcut keys | ctrl a to z shortcut keys
A.S Computer Education
3.4M views

0:40
Public keys vs. Private keys (in less than a minute 😉)
Trezor
1.7K views

10:05
Secure IoT Messaging with Symmetric Keys: A Simplified Guide
LEARNACON
79 views

3:22
How to Secure App-Level Encryption Keys with Unbound Key Control (UKC) via REST API
Unbound Security
564 views

5:58
Module 4.9. Distribution of Secret Keys Using Public-Key Cryptography|S8 ECE | SECURE COMMUNICATION
bushara abdulrahim
2.6K views

6:05
Secure Pixel Secrecy Embedding Secret Keys with Python and LSB Steganography in Images
1Crore Projects
4 views

1:47
Secure Your Cryptographic Keys in the Cloud with Cryptomathic's Enclave Security Module (ESM)
CRYPTOMAThIC
225 views

1:53
Secure API Keys with a Public-Key Cryptography on Android (Online Course)
Stevdza-San
3.6K views
3:01
How To Secure And Rotate Cryptographic Keys In Encryption Protocols?
Internet Infrastructure Explained
1 views

25:46
Understanding the role Cryptographic Keys in the IoT Secure World
Secure Thingz
2.7K views

4:10
Difference between Computationally Secure and Unconditional Secure Cipher | Information Security
Easy Engineering Classes
6.4K views
![Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]](/image/i.ytimg.com/vi/Hs-7ixoSqAA/xhqdefault.jpg.pagespeed.ic.BPwrxXKFrf.jpg)
41:29
Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]
Microsoft Research
77 views

0:13
Difference between unconditionally secure and computationally secure in cryptography and .....
SUKANYA BASU
973 views

0:55
Overview of Secure Aggregation #ai #artificialintelligence #machinelearning #aiagent Overview Secure
NextGen AI Explorer
12 views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

0:05
Read Secure Software and Comm. on Handheld Devices: Secure Software and Communication on Handheld
Isaksen
2 views

2:05
Secure USB Flash Drive - SanDisk Enterprise Secure ...
John Objet
1 views

4:53
Best browser for privacy 2021 | Iridium Browser | A browser securing your privacy | Most Secure Web Browsers That Protect Your Privacy | most secure browser 2021
FOCUS EXCLUSIVE
13 views

46:18
Roll Your Own Secure Cloud Storage with SSHFS - Secure Shell File System - Hak5
Hak5
5 views

3:39
Medical Coding Services | Secure Medical Coding & Secure Medical Data Handling
PDNSeek .com
5 views

0:25
A Secure Erasure Code-Based Cloud Storage System with Secure Data Forwarding
satish20059
259 views