Search Results for "Secret Sharing Scheme"
Find videos related to your search query. Browse through our collection of videos matching "Secret Sharing Scheme". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Secret Sharing Scheme"
50 results found

5:06
10th class computer pairing scheme 2024 |10th class computer scheme 2024 | 10th computer scheme 2024
Shahid Iqball
50 views

7:13
10th class biology pairing scheme 2024 | Class 10th biology Scheme 2024 | 10th biology scheme 2024
Shahid Iqball
320 views

8:20
K-N SECRET SHARING VISUAL CRYPTOGRAPHY SCHEME FOR COLOR IMAGE USING RANDOM NUMBER
JP INFOTECH PROJECTS
7.4K views
5:19
A New K Out Of N Secret Image Sharing Scheme In Visual Cryptography - 1Crore Projects
1 Crore Projects
634 views
14:53
Visual Secret Sharing Scheme for Digital Image Watermarking
IJERT
67 views

15:15
Visual Secret Sharing Scheme: Visual Cryptography
Pavani K
94 views
0:54
What is Shamir’s Secret Sharing Scheme in crypto?
Crypto Like A Pro
654 views
12:41
Encrypting your Safex Private Key with Shamir's Secret Sharing Scheme
Safex News
660 views

0:07
Read Proxy Blind Multi-Signature Scheme: Proxy Blind Multi-signature Scheme Using Elliptic
Isaksen
0 views

9:47
Ponzi scheme explained simply Urdu Hindi _ How pyramid scheme works_ _Ponzi schemes India Pakistan
Dr Muhammad Farooq Buzdar
61 views
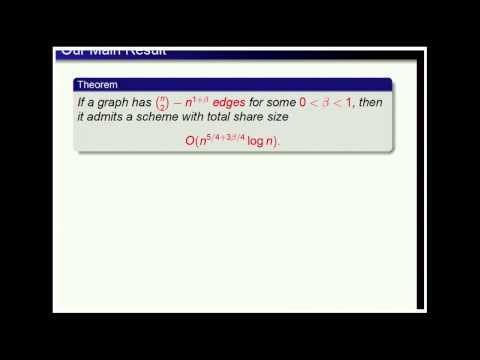
19:14
Secret Sharing Schemes for Very Dense Graphs
IACR
572 views

0:38
Shamir's Secret Sharing The 1979 Algorithm Securing Your Crypto in 2025
Cypherock
395 views

31:43
Data Hiding with Encrypted Multi Secret Sharing using Modified LSB Technique
IJERT
167 views

4:31
ppt for secret sharing
Keerthika Manoharan
214 views

24:58
Large Message Homomorphic Secret Sharing from DCR and Applications
IACR
339 views
3:15
Shamir's Secret Sharing 360p
Avishek Prasad
124 views
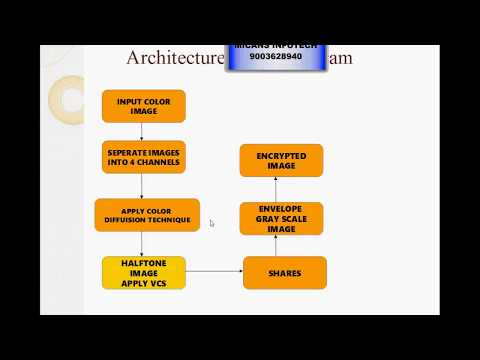
0:57
Halftoning Visual Cryptography Using Secret Sharing
MICANS INFOTECH PVT LTD
669 views
22:05
Traceable Secret Sharing and Applications
IACR
627 views
7:07
Secured document generation using QR Code and Visual Secret Sharing
bala venkat
400 views
20:42
The Rise of Paillier: Homomorphic Secret Sharing and Public-Key Silent OT
IACR
1.2K views
8:51
A Secret-Sharing-Based Method for Authentication of Grayscale Document Images via the Use of the PNG
JP INFOTECH PROJECTS
1.6K views
0:16
Visual Cryptography Using K-N-Secret-Sharing
PhD Research Labs
231 views
2:54
Shamir Secret Sharing GUI
Sam Hakim
955 views
2:36
A Secured key based secret data sharing system in Steganography
Students Project
142 views
52:41
Secret Sharing Schemes
nptelhrd
21.2K views

20:50
Homomorphic Secret Sharing from Lattices Without FHE
IACR
714 views

1:07:48
MPC-TP: Homomorphic Secret Sharing - Part I - Yuval Ishai
CrIS Lab IISc
696 views

18:36
Secret Sharing, Rank Inequalities and Information Inequa ...
IACR
214 views
6:38
Final Year Projects | A Secret-Sharing-Based Method for Authentication of Grayscal
ClickMyProject
107 views

1:19
Secret Sharing - Applied Cryptography
Udacity
21.7K views

42:33
Amos Beimel: Are There Efficient Secret Sharing Schemes?
The Open University of Israel
769 views
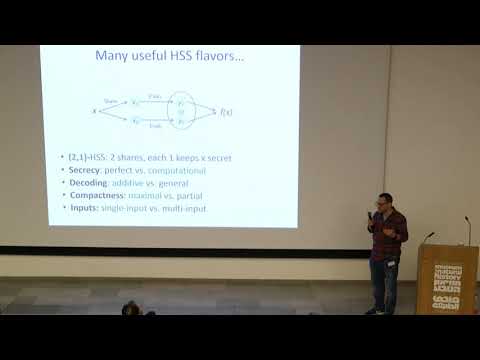
48:23
Yuval Ishai (Technion): Homomorphic Secret Sharing
Computational Complexity
445 views

26:48
Secret sharing
Mihir Bellare
929 views

0:37
Download Visual Cryptography and Secret Image Sharing Ebook {EPUB} {PDF} FB2
Angela Young
27 views

0:07
Download Visual Cryptography and Secret Image Sharing (Digital Imaging and Computer Vision)
Viktoria Alterman
5 views

0:07
Read Visual Cryptography and Secret Image Sharing (Digital Imaging and Computer Vision) Ebook
Lsachs
1 views
4:20
2012 IEEE A Secret-Sharing-Based Method for Authentication of Grayscale Document Images via the Use of the PNG Image with a Data Repair Capability
IEEE Projects 2012
116 views
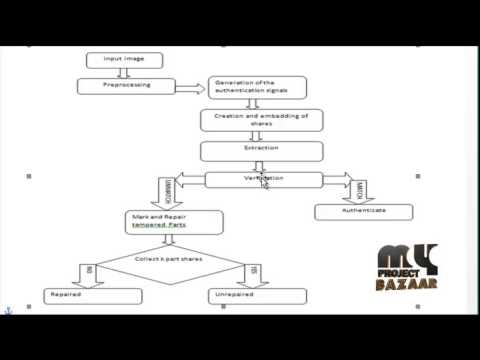
6:40
Final Year Projects | A Secret-Sharing-Based Method for Authentication of Grayscale
MyProjectBazaar
57 views
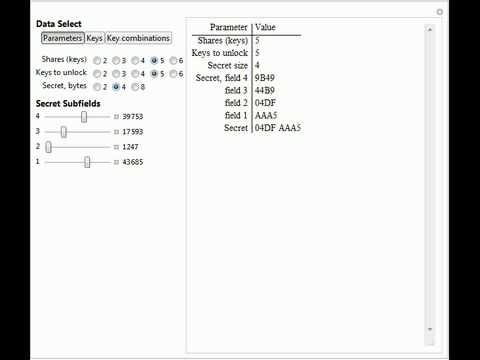
0:41
Encrypted Secret Sharing
Wolfram Demonstrations Project
245 views
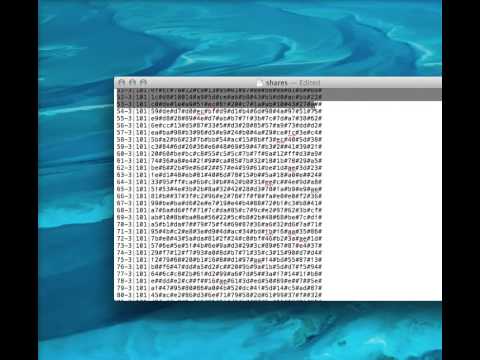
3:46
Shamir Secret Sharing CLI
Sam Hakim
483 views

6:43
Image processing-Visual cryptography scheme for secret color images with color QR codes
MyProjectBazaar EGC
14 views

6:42
Matlab Project Visual cryptography scheme for secret color images with color QR code-ClickMyProject
ClickMyProject
217 views

1:34
Vídeos Secret Story 5 Célia já acusa saudades Secret Story 5 TVI Site Secret Story 5
Secretstory.pt
1.7K views

5:07
Vídeos Secret Story 5 Célia já pensa em desistir Secret Story 5 TVI Site Secret Story 5
Secretstory.pt
1.7K views

0:54
Vídeos Secret Story 5 O que significam as frases da CASA Secret Story 5 TVI Site Secret Story 5
Secretstory.pt
386 views

0:11
Vídeos Secret Story 5 Agnes «O Daniel bateu me na mama» Secret Story 5 TVI Site Secret Stor
Andresa Natário
536 views

6:17
Secure QR-Code Based Message Sharing System Using Cryptography and Steganography
SHOAIB SHAIKH
633 views
0:53
Delete This Info Before Sharing Any Photo! #shorts #cybersecurity #shortvideo
Akanksha Kumari
72 views

32:28
17-How Public Key Distribution Works? 💡 | Secure Key Sharing in Network Security
Sundeep Saradhi Kanthety
107.5K views
0:20
Adaptive Active Power Sharing Techniques for DC and AC Voltage Control in a Hybrid DC AC-2019-20
MATLAB ASSIGNMENTS AND PROJECTS
18 views