Search Results for "Lec 2"
Find videos related to your search query. Browse through our collection of videos matching "Lec 2". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Lec 2"
51 results found

51:09
FNATIC POBY DEBUT IN THE LEC VERSUS HERETICS - LEC SUMMER 2025
Caedrel
343.2K views

5:41
symmetric Encryption principles| ITphile|lec 3
ITphile
478 views

16:56
Lec-12: DFA (Part-2) | What is DFA in TOA with examples in hindi/urdu | DFA in TOC | Finite Automata
YZ Tutorials
162 views

53:26
Mod-01 Lec-01 GRAMMARS AND NATURAL LANGUAGE PROCESSING
nptelhrd
389.0K views
58:30
Lec-24 Traveling Salesman Problem(TSP)
nptelhrd
508.7K views
19:31
Lec 59 Cyclic Groups and Discrete Logarithm
NPTEL - Indian Institute of Science, Bengaluru
509 views

24:37
Information Security Lec 05: Low, Moderate & High Security Levels | Computer Security Challenges
Tech CS&IT
2.2K views

3:31
Can You HIDE a SECRET PAYLOAD in a JPEG Image? - Lec 27
Hack Sphere X
5.9K views

53:27
Lec 9 | MIT 18.085 Computational Science and Engineering I, Fall 2008
MIT OpenCourseWare
27.9K views
48:04
Lec 6: Velocity, acceleration; Kepler's second law | MIT 18.02 Multivariable Calculus, Fall 2007
MIT OpenCourseWare
252.5K views

1:04:54
CSE104, Computational Complexity: Lec 1, Cantor's diagonalization
C. Seshadhri
1.0K views

56:49
Lec 2 | MIT 18.085 Computational Science and Engineering I
MIT OpenCourseWare
20.4K views
9:07
Complexity Classes | P & NP classes | TOC | Lec-96 | Bhanu Priya
Education 4u
197.8K views

35:47
Cryptography & Network Security | Unit-2 | Lec-2 | One Shot | KCS-074 | Aktu Exams| PYQ Solutions
Multi Atoms
10.3K views

51:37
Lec 3: Bias-Variance Tradeoff
NPTEL IIT Guwahati
16.3K views
13:53
Lec-13: NFA to DFA (Part 2) | Explained in Detail | YZTutorials
YZ Tutorials
120 views

17:48
Lec 17: Preemptive Priority Scheduling Algorithm in OS with example | Operating System
Jenny's Lectures CS IT
548.3K views

1:16:07
CSE104, Lec 2: Turing machine simulations
C. Seshadhri
730 views

19:29
POBY DEBUT GAME in the LEC | FNC vs TH Voicecomms
FNATIC
80.5K views
9:55
Lec-18 - Network Security - (Hill Cipher - Encryption)
Dr. Mohammed Abdalla Youssif
13 views

50:10
Lec 12: Gradient; directional derivative; tangent plane | MIT 18.02 Multivariable Calculus, Fall 07
MIT OpenCourseWare
261.7K views

1:13:06
The Advent of Europeans | Lec 01 | Modern History | Lakshya IAS 2026
StudyIQ IAS
5.7K views

59:33
Mod-01 Lec-11 Regular expressions, they denote regular languages.
nptelhrd
24.4K views

8:31
CCS | Unit-1 | Lec-01 | Introduction to Computer Security
s kalaivani
270 views

5:51
Lec-9: Operators in Python 🐍 Precedence & Associativity with examples | Python for Beginners
Gate Smashers
166.5K views
8:00
Lec 4 Turing Machine Example2
Shibaji Paul
25.1K views

11:14
Substitution Cipher Method class 9 || 9th computer ch 4 lec 5 || urdu / hindi
Muhammad Kaleem Haider
176 views

12:55
Tuples in Python | 11th Computer - Chapter 2 - Lec 23
Academics with AB
6.7K views

59:03
Mod-06 Lec-32 PROBLEMS AND INSTANCES , UNIVERSAL TM , DECIDABILITY
nptelhrd
21.1K views
17:36
TOC Lec 43-Turing machine problem Palindrome by Deeba Kannan
DEEBA KANNAN
216.3K views

52:18
Lec 10: Second derivative test; boundaries & infinity | MIT 18.02 Multivariable Calculus, Fall 2007
MIT OpenCourseWare
228.4K views
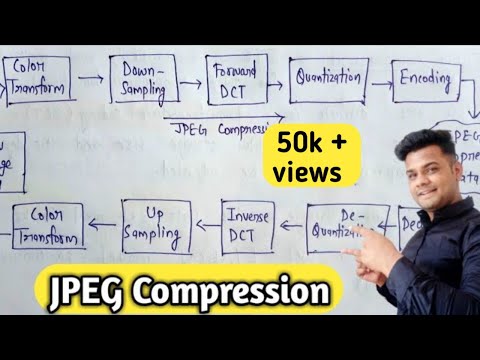
6:27
JPEG Compression in digital image processing | Lec-31
Er Sahil ka Gyan
66.0K views

14:32
Converting CFG to GNF | Example-1 | TOC | Lec-73 | Bhanu Priya
Education 4u
475.9K views
53:53
Mod-13 Lec-03 Undecidability2
nptelhrd
1.6K views

8:59
Lec-3: Types of Logic Gates | Symbols | Truth Tables
Gate Smashers
1.6M views

7:57
Lec-14: DFA vs NFA in TOC in Hindi with examples | Must Watch
Gate Smashers
1.1M views

34:31
Lec 25: Sequential Decision Problems
NPTEL IIT Guwahati
11.0K views

11:02
TOC Lec 46-Multiplication in turing machine using subroutines by Deeba Kannan
DEEBA KANNAN
90.9K views
4:07
Personal Computing system | OS | Lec-09 | Bhanu Priya
Education 4u
94.8K views

25:36
Cryptography and Network Security I \ Lec. 7 \ ( RC4 , RC5 and Blowfish Algorithms)
Dr. Ali J. Abboud
1.4K views

32:44
JNTUK R16 III CSE SEM2 CYBER SECURITY UNIT 4 INTRODUCTION TO TOOLS & METHODS USED IN CYBER CRIME LEC
RVIT — Autonomous, Guntur
1.8K views
56:03
Mod-06 Lec-01 Variants of FA
nptelhrd
675 views

57:15
Lec 3 | MIT 18.085 Computational Science and Engineering I
MIT OpenCourseWare
15.1K views
36:02
Mod-13 Lec-01 Decidability
nptelhrd
1.8K views
9:43
Caesar Cipher Explained with Solved Example|lec 3|urdu|hindi
ITphile
379 views

1:01:04
Mod-01 Lec-02 Introduction to finite automaton.
nptelhrd
93.0K views

50:50
Lec 5: Parametric equations for lines and curves | MIT 18.02 Multivariable Calculus, Fall 2007
MIT OpenCourseWare
315.7K views
54:31
Mod-10 Lec-01 Pushdown Automata
nptelhrd
1.7K views

50:03
Cryptography & Network Security | Unit-3 | Lec-2 | One Shot | KCS-074 | Aktu Exams| PYQ Solutions
Multi Atoms
11.8K views

16:58
Deterministic Finite Automata|LEC-7|Formal Languages andAutomata Theory, VTU syllabus module - 1
Vijaya Prasad Lectures
2.6K views
30:58
LEC#2 BASE AND DERIVED QUANTITIES
Learn by Lectures
232 views
Page 1 Next