Search Results for "Cyber Regulations"
Find videos related to your search query. Browse through our collection of videos matching "Cyber Regulations". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Cyber Regulations"
50 results found

16:01
Cyber Forensics||Meaning||Process Of Cyber Forensics||Rules||Applications||Cyber security||Cyber||
Study For Dreams 23
35.2K views

9:30
Cyber Forensic vs Cyber Security | Know the Difference between Cyber Security and Cyber Forensic
FORnSEC Solutions
23.7K views

9:32
Top 10 Cyber Attacks In History | Biggest Cyber Attacks Of All Time | Cyber Security | Simplilearn
Simplilearn
359.4K views

3:44
Cyber security क्या है? | What is Cyber Security in Hindi? | Why Cyber Security is Important?
Deepak TechTimes
59.8K views

7:07
What Is Cyber Security | How It Works? | Cyber Security In 7 Minutes | Cyber Security | Simplilearn
Simplilearn
4.8M views

0:07
cyber security 🔐 workshop review | cyber kaksha | cyber security for beginner
Cyber Kaksha
1.8K views

0:19
What is Cyber Security in urdu | cyber security introduction #cyber #cybersecurity #computer #shorts
ABID FAROOQ BHUTTA
27.2K views

2:34
Top 5 Cyber Security Tools | Tools For Cyber Security | Top Cyber Security Tools | Intellipaat
Intellipaat
10.2M views

0:05
Read Cyber Security Cyber Crime and Cyber Forensics: Applications and Perspectives Ebook Free
Reimold
3 views

0:08
Read Cyber Security Cyber Crime and Cyber Forensics: Applications and Perspectives PDF Online
Myrthenbaum
2 views

4:53
Cyber Security in hindi | Cyber security | What is cyber security
hackploit
18 views

3:33
Cyber Security: आप पर भी हो सकता है Cyber Attack, ऐसे करें बचाव | Cyber Attack News | वनइंडिया हिंदी
Oneindia Hindi | वनइंडिया हिन्दी
14 views

2:00:20
🔴Cyber Security Unit 3 One shot | Tools and Methods used in cyber crime | Cyber Security BCC301/401
EduShine Classes - Arman Ali
40.3K views

3:08
What is Cyber Kill Chain | Cyber Security | Short Intro | Defense Against Cyber Attacks
Techie AB
121 views

12:12
CISA, CISM, CISSP - Security Regulations, Standards, Frameworks
CYVITRIX LEARNING
35 views

3:56
Why Are Quantum Cryptography Regulations Challenging? - Quantum Tech Explained
Quantum Tech Explained
2 views
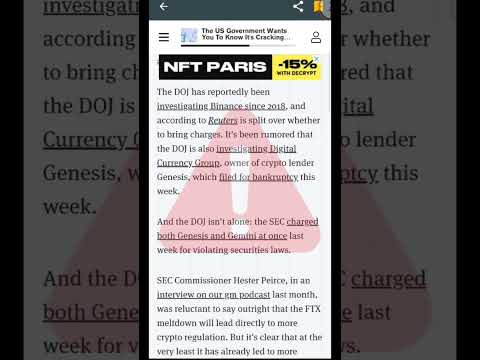
1:00
🚨Warning: #USA #Crypto Crackdown!!🚨 #XRP #XDC #XLM #Crypto #FTX #Regulations #USDT #Shorts
Crypto Ready
391 views

8:16
Crypto News Today: Cryptocurrency in India Latest Update Hindi| Supreme Court | Crypto Regulations
Switch
44.6K views

1:24
Are there global warming laws and what do they do?: Global Warming Laws And Regulations
Scribble
0 views

0:07
Read Practical Guide for the major trading countries and regions. the food additive regulations
Bella Foley
0 views
![Why we need environmental regulations [Mic Archives]](/image/s1.dmcdn.net/v/Jlcvs1e9Jg9VycZUi/x720)
0:52
Why we need environmental regulations [Mic Archives]
Mic
278 views

1:10
Crypto Updates - Robinhood Launches App, Crypto Regulations In UK, Crypto Investor Analysis
VishalGuptaOrg
38 views

3:56
Government Announces Implementation Of New Tea Regulations
EbruTVKENYA
6 views

3:17
Lockdown restriction and regulations in Kerala | Oneindia Malayalam
Oneindia Malayalam
2.6K views

2:04
Cryptocurrency: What are the regulations across the world?
India Today
7 views
0:45
Crypto Consumer Advocacy Group rallies Investors to Challenge SEC Regulations
Benzinga
1 views

10:18
Padu: Govt agencies bound by own data regulations, says Rafizi in slamming LFL
The Star
1.3K views

0:49
European Parliament passes 'historic' AI regulations
CGTN Europe
810 views

1:31
Title IX Regulations Add Protections for Transgender Students
Wibbitz Politics News
926 views

5:28
'Food Security Is National Security': Britt Questions EPA Administrator On Recent Regulations
Forbes Breaking News
322 views

2:15
Screen composers fight for better regulations around music generated by artificial intelligence
ABC NEWS (Australia)
237 views

3:25
Malaysia plans national cloud policy, AI regulations
The Star
343 views

2:13
Trump Signs New Stablecoin Regulations into Law, a Major Milestone for Crypto Industry
TIME
245 views

0:46
FCC Reverses Trump-era Decision, Reinstates Net Neutrality Regulations Prohibiting ISPs from Prioritizing Traffic
Benzinga
331 views
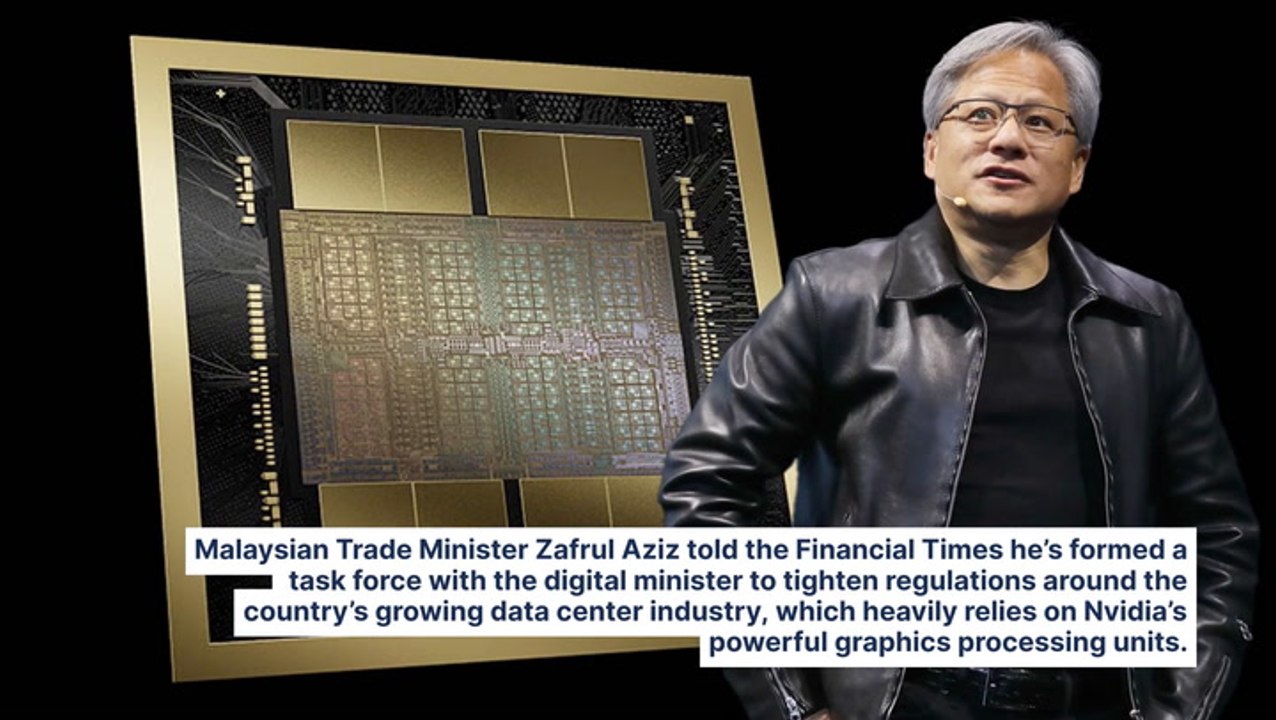
0:47
Nvidia Chip Flows Under Scrutiny As Malaysia Moves To Tighten Regulations Amid US Export Controls On China
Benzinga
290 views

34:32
Steganography For Cyber Security Day 01 || Sonargaon University Cyber Security Batch 01
BinaryGuardians
112 views

0:59
Top 3 Biggest Cyber Attacks In History | Cyber Security | Intellipaat
Intellipaat
10.6K views

3:30
Cyber-bullying Facts – Top 10 Forms of Cyber Bullying
Kaspersky
770.0K views

1:27
Steganography in Cyber Security | Steganography in Cyber Security Projects
NetworkSimulationTools
75 views

5:57
Trojan horse in cyber security | trojan in cyber security | Lecture 30
Simply Made
55.9K views

5:11
What Is CYBER CRIME | Cyber Crime Explained
Tech Might
60.7K views

0:59
How to Become a Cyber Security Analyst in 2024? | Cyber Security | Intellipaat #Shorts
Intellipaat
130.3K views

1:51
Paid Workshop on Cyber Security on 26 September 2021 | Indian Cyber Sec
Indian Cyber Sec
31 views

0:14
What is Cyber Forensics | Digital Evidence | Data acquisition | Phases of Cyber Forensics
Cyber Pathshala India - Cyber Security Training
13.4K views

5:19
What Is Cryptology & Cyber Security? What Is The Main Concept Of Cryptology & Cyber Security?🎭📂🖥️
Technical Supradip
302 views

32:44
JNTUK R16 III CSE SEM2 CYBER SECURITY UNIT 4 INTRODUCTION TO TOOLS & METHODS USED IN CYBER CRIME LEC
RVIT — Autonomous, Guntur
1.8K views

13:45
COURSERA:INTRODUCTION TO CYBER SECURITY TOOLS AND CYBER ATTACKS | WEEK 3:KEY CONCEPTS| QUIZ ANSWERS
Anand Ranjit Kumar Mukkala
15.0K views

11:14:05
Cyber Security Full Course FREE | Cyber Security Course 2026 | Intellipaat
Intellipaat
10.3K views

4:27
||What is Stenography In Cyber Security?||Types Of Steganography||Cyber Security|| By-@cyberwire09
CYBERJET
206 views

5:15
Inside AIS-189: How India’s Cars Are Getting Cyber-Protected || Cyber Attacks || Cryptography
Gettobyte
2 views
Page 1