Search Results for "Cyber Physical Systems"
Find videos related to your search query. Browse through our collection of videos matching "Cyber Physical Systems". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Cyber Physical Systems"
50 results found

4:20
Difference Between Social Distancing and Physical Distancing | What is Physical Distancing? | Physical Distancing Vs. Social Distancing
Beyond Shiksha
2 views

2:39
Winners Defence Academy Physical Training SSC GD MP Police Constable Delhi Police Physical Army Physical
DJ Sachin Guna
0 views

0:30
About For Books Principles of Cyber-Physical Systems For Kindle
dm_c64defac2b3b72cd450566e9d9eebae8
0 views

16:01
Cyber Forensics||Meaning||Process Of Cyber Forensics||Rules||Applications||Cyber security||Cyber||
Study For Dreams 23
35.2K views

9:30
Cyber Forensic vs Cyber Security | Know the Difference between Cyber Security and Cyber Forensic
FORnSEC Solutions
23.7K views

0:18
Introduction to Physical Education and Sport Introduction to Careers in Health Physical PDF
Dearthe29
1 views

22:11
Lindsey Physical Exam - Pediatric Physical Exam
Rawiz
20.7K views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

9:32
Top 10 Cyber Attacks In History | Biggest Cyber Attacks Of All Time | Cyber Security | Simplilearn
Simplilearn
359.4K views

3:44
Cyber security क्या है? | What is Cyber Security in Hindi? | Why Cyber Security is Important?
Deepak TechTimes
59.8K views

7:07
What Is Cyber Security | How It Works? | Cyber Security In 7 Minutes | Cyber Security | Simplilearn
Simplilearn
4.8M views

0:07
cyber security 🔐 workshop review | cyber kaksha | cyber security for beginner
Cyber Kaksha
1.8K views

0:19
What is Cyber Security in urdu | cyber security introduction #cyber #cybersecurity #computer #shorts
ABID FAROOQ BHUTTA
27.2K views

2:34
Top 5 Cyber Security Tools | Tools For Cyber Security | Top Cyber Security Tools | Intellipaat
Intellipaat
10.2M views

0:05
Read Cyber Security Cyber Crime and Cyber Forensics: Applications and Perspectives Ebook Free
Reimold
3 views

0:08
Read Cyber Security Cyber Crime and Cyber Forensics: Applications and Perspectives PDF Online
Myrthenbaum
2 views

4:53
Cyber Security in hindi | Cyber security | What is cyber security
hackploit
18 views

3:33
Cyber Security: आप पर भी हो सकता है Cyber Attack, ऐसे करें बचाव | Cyber Attack News | वनइंडिया हिंदी
Oneindia Hindi | वनइंडिया हिन्दी
14 views

2:00:20
🔴Cyber Security Unit 3 One shot | Tools and Methods used in cyber crime | Cyber Security BCC301/401
EduShine Classes - Arman Ali
40.3K views

3:08
What is Cyber Kill Chain | Cyber Security | Short Intro | Defense Against Cyber Attacks
Techie AB
121 views

8:30
Solving linear systems by graphing | Systems of equations | 8th grade | Khan Academy
Khan Academy
1.1M views

4:57
Condition for Resource Deadlocks-Operating Systems-UNIT – 4 Deadlocks and File Systems-20A05402T
D Sumathi
2.7K views

3:42
GuardMe Security - Home Security Systems & Commercial Security Systems
Craig Metzger
5 views

0:18
Replication Techniques in Distributed Systems Advances in Database Systems PDF
Prelf1983
1 views
![[PDF Download] Managing Risk In Information Systems (Information Systems Security & Assurance)](/image/s2.dmcdn.net/v/DB1S81e0J9e8R5SHb/xx720.pagespeed.ic.B6QP-QHvYN.jpg)
0:07
[PDF Download] Managing Risk In Information Systems (Information Systems Security & Assurance)
Zqleukji
1 views

0:17
Read Embedded Systems Security Practical Methods for Safe and Secure Software and Systems
Limral9668
1 views

0:07
Download The Systems View of the World: A Holistic Vision for Our Time (Advances in Systems
Kamila9992
2 views

0:07
Read Managing Risk In Information Systems (Information Systems Security & Assurance Series)
Tsereteli Lia
0 views

0:36
PDF Expert Systems in Law Systems with Legal Examples EBook
DaiseyBridgeman
2 views

0:08
Read Modeling Embedded Systems and SoC's: Concurrency and Time in Models of Computation (Systems
Lelag Ispiryan
0 views

0:08
Read Algorithms for Sensor Systems: 6th International Workshop on Algorithms for Sensor Systems
Tkarapetian
0 views

0:08
Read Managing Risk In Information Systems (Information Systems Security & Assurance Series)
Bbuhler
0 views

0:07
Download Managing Risk In Information Systems (Information Systems Security & Assurance Series)
Maisi Baker
3 views

0:50
Security systems in Kengeri| security systems in Bangalore
Sravani Chalamkota
2 views

0:55
Security systems in Kengeri| Security systems in Kadugodi
Sravani Chalamkota
7 views

3:16
lay betting systems betfair laying systems
nufcsafc77
210 views

7:28
Types of systems and the meaning and structure of linear systems
yourthoughts
41 views

16:04
Class 9 Maths Chapter 1 Number Systems Exercise 1.1 Solution | Number Systems Ex 1.1 solution || Class 9 Maths Ch-1 Ex 1.1 solution#mathssolution #hmsbkipadhai
HM SB KI PADHAI
20 views

24:27
Class 9 Maths Chapter 1 Number Systems Exercise 1.2 Solution |Number Systems solution #mathssolution
HM SB KI PADHAI
15 views

34:52
Class 9 Maths Chapter 1 Number Systems Exercise 1.3 Solution |Number Systems solution #mathssolution
HM SB KI PADHAI
14 views

0:32
Fx Systems Reviews | Fx Systems
forexsystems411
5 views

18:49
Solving Systems of Equations by Substitution | Solving Linear Systems | Partners in Prime
Partners in Prime
51.7K views

9:11
Public & Private Key Steganography - Explained | Stego-Systems | Steganography | Cyber Nation
Cyber Nation
499 views
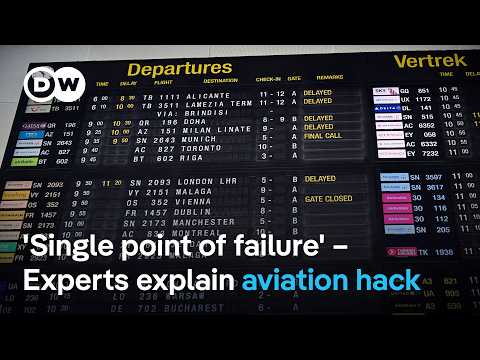
11:07
Cyber attacks targeting check-in and baggage systems cause mass chaos at European airports | DW News
DW News
85.6K views

1:12
Marcos orders PNP: Bolster PH cyber security systems
Manila Bulletin
844 views

34:32
Steganography For Cyber Security Day 01 || Sonargaon University Cyber Security Batch 01
BinaryGuardians
112 views

0:59
Top 3 Biggest Cyber Attacks In History | Cyber Security | Intellipaat
Intellipaat
10.6K views

3:30
Cyber-bullying Facts – Top 10 Forms of Cyber Bullying
Kaspersky
770.0K views

1:27
Steganography in Cyber Security | Steganography in Cyber Security Projects
NetworkSimulationTools
75 views

5:57
Trojan horse in cyber security | trojan in cyber security | Lecture 30
Simply Made
55.9K views