Search Results for "Vulnerability exploitation"
Find videos related to your search query. Browse through our collection of videos matching "Vulnerability exploitation". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Vulnerability exploitation"
50 results found
0:24
What is Vulnerability? Types of Vulnerability in Cybersecurity
a2zOfCloud
2.5K views

0:24
Binary Exploitation vs. Web Security
LiveOverflow
503.9K views

10:41
USENIX Security '20 - TeeRex: Discovery and Exploitation of Memory Corruption Vulnerabilities...
USENIX
668 views

2:33
Lawmakers Lament Alleged Exploitation Of Electricity Consumers By DisCos
TVC News Nigeria
397 views

13:36
Hacking Fundamentals: Enumeration And Exploitation
TheHackingLab
211 views

26:27
Steganography and SUDO exploitation | Agent Sudo TryHackMe
Motasem Hamdan
1.8K views
3:06
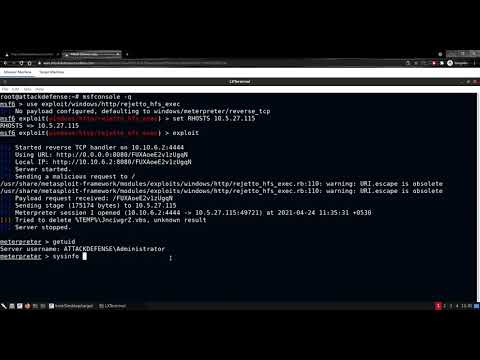
Post Exploitation With Metasploit Lab Walkthrough: FakeLogonScreen
Pentester Academy TV
1.2K views
0:37
🔒 Protect your computer from unauthorized access and data exploitation by turning off these.
Computer Geeks
1.5K views
0:41
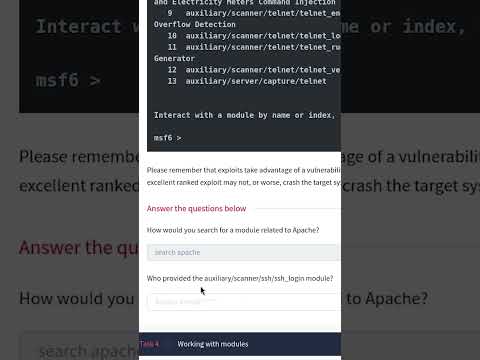
Windows Exploitation Basics: Msfconsole | Answer the Questions Series #shorts #thm #tryhackme
CyberTodd
102 views

1:48
BROWSER EXPLOITATION MEME
Jo Praveen
250 views
27:06
Shmoocon 2013 - Hide and Seek, Post-Exploitation Style
theprez98
1.7K views

3:45
Meterpreter - Advanced Exploitation, Kali Linux Full Course (Part 28) by Pakfreedownloadspot.blogspot.com
HD Movies Only
95 views
18:14
Website Security and Exploitation in Urdu/Hindi
SUPER BEST
842 views

0:06
PDF Exploitation of Illness in Capitalist Society (The Bobbs-Merrill studies in sociology)
Gustavemanuel
1 views

5:33
Sandrine Murcia (Cosmian): Cosmian, une nouvelle approche de l'exploitation des données via le chiffrement - 08/01
BFM Business
17 views

1:45
Un député australien met le feu à une rivière pour dénoncer l'exploitation du gaz de couche
OhMyMag FR
6 views

24:25
The Future Is Female: Image-Based Sexual Abuse — Fighting Deepfake Exploitation
AWANI
61 views

1:34:32
American Sweatshop 2025 full mystery thriller movie Lili Reinhart Daniela Melchior Joel Fry #AmericanSweatshop #Drama #DocumentaryStyle #SocialDrama #WorkersRights #Exploitation #EconomicStruggle #Gritty #Realism #IndieFilm #2025Movie #Powerful #ThoughtP
Daily Movies
126 views

1:45:30
Supervixens 1975 | Exploitation Film | Shari Eubank
moviextreme2024
106 views

2:52
Practical Exploitation - Intro
practicalexplt
33 views
3:20
4LYN - Club Exploitation (Official Music Video)
4LYNTV
180 views

5:19
php Calc | Web Exploitation | GrabCON CTF 2021
Rahul Singh Chauhan
1.5K views

1:33
Deux artistes nigérians accusent leur label d’escroquerie et d’exploitation
Brut Afrique
571 views

1:29
Exploitation des marais de cyprès en Caroline du Nord : entre secrets millénaires et équilibre naturel !
Futura
430 views

1:24:12
The Last House on the Left (1972) A Shocking and Raw Exploitation Thriller
Classic Channel
9.7K views

8:30
Silk Typhoon Member Arrested, Chromium Vulnerability & Call of Duty | cybernews.com
Cybernews
12.6K views
2:26
Unauthorized Access Admin Panel Vulnerability
Ibnu Fachrizal
230 views

0:48
Cryptographic Vulnerability?. #cybersecuritylearning #cyber fundamentals #cyber101
a2zOfCloud
25 views
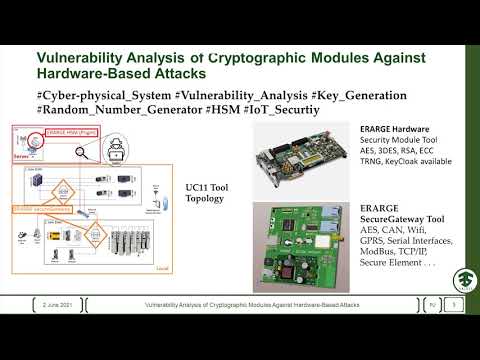
4:18
Vulnerability Analysis of Cryptographic Modules Against Hardware-Based Attacks
VALU3S Project
146 views

0:16
Secp256k1 DHEC vulnerability
teknopath aka moonshine
374 views

12:12
OSI Security Architecture - Attacks, Services, Mechanisms, Vulnerability, Threats, Risk
Mukesh Chinta
501 views

20:50
The Power of Vulnerability | Brené Brown | TED
TED
23.9M views

47:05
Lecture 2 | Goals of Security, Vulnerability & Threat | Cryptography and System Security
Sridhar Iyer
1.3K views

2:26
Strengthening Cyber Defenses: CISA’s Free Vulnerability Scanning Explained
CISA
4.2K views

10:14
Diffie-Hellman Key Exchange Vulnerability
Mert Özbay
334 views

0:16
Buffer Overflow Explained: Breaking Down the Code Vulnerability! #short #shortvideo #shorts
Aarnaaology
147 views
0:27
Vulnerability Scanning Tools #shorts
ZeroDay Vault
87 views
4:13:07
SOC100 Class 20 - Vulnerability Management, Cryptography, Symmetric & Asymmetric Encryption Part 1
Level Effect
534 views

7:10
Cybergang Shutdown, Linux Vulnerability & Microsoft | Weekly News
Cybernews
9.4K views
0:59
What is Cross Site Scripting (or XSS) Vulnerability in Cybersecurity
Learn with Whiteboard
56.5K views

0:52
Exploiting CSRF Vulnerability
the security vault
109 views

0:58
Orca CEO Insights | Vulnerability Management and Risk Prioritization
Orca Security
112 views

4:50
Stop using Cursor NOW. Major security vulnerability.
Goju Tech Talk
112.7K views
32:41
Your AI Vulnerability: The Psychological Trap of Talking to AI
Verlicity AI
8 views
41:27
OL: Vulnerability
jamesbarber4
178 views

24:51
AI-Enabled Post-Quantum Cryptography Migration: Trust and Vulnerability Discovery - Mark Tehrani
Bill Buchanan OBE
314 views

2:27
Stay advanced with promisec Vulnerability Scanning Tools
Alan Taylor
4 views

4:30
Why Vulnerability Testing Is Important
SURESH sur5031
0 views

0:55
Lizzo: Vulnerability is important
Bang Showbiz Extra
154 views

10:52
Krack Attacks (WiFi WPA2 Vulnerability) - Computerphile
qwak1234
1 views