Search Results for "Secure Logging"
Find videos related to your search query. Browse through our collection of videos matching "Secure Logging". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Secure Logging"
50 results found

3:36
What Is Secure Logging? - Next LVL Programming
NextLVLProgramming
67 views
7:15
How to secure Gmail ? || Gmail ko secure kaise kare ?क्या आपका Gmail Secure है ?
DoWithMe Start Learning
1 views

4:58
TryHackMe OWASP Top 10 Insufficient Logging and monitoring | CTF | Walkthrough
Kumar Atul Jaiswal
161 views
0:53
how to download from scribd without even logging in
Mohammad Farshoukh
110.0K views
![[NG:RP] Logging to avoid Iheb Hlif](/image/i.ytimg.com/vi/FmvThqWI-80/hqdefault.jpg)
0:07
[NG:RP] Logging to avoid Iheb Hlif
Frank Sezam
20 views

0:16
Ms500i mit einer 90cm Schiene... #forest #forstwirtschaft #wirliebenholz #forsttechnik #logging
im-wald de mit Sinn und Verstand
13.2K views
3:11
Automated Attendance Logging System - Face Recognition | AI Class 12 Capstone Project
J By Tech
134 views
31:41
"Diagnostics - Seeing Inside Your Application Without Logging" - Jeremy Rotstein (PyCon AU 2023)
PyCon AU
1.0K views

1:47
Kerala Floods: Many Dead As Incessant Rainfall Causes Landslides, Water logging
OTV News
212 views

2:07
Chennai Rain: Heavy rain causes water logging, Flood alert issued | Oneindia News
Oneindia
551 views

2:44
FATAL LOGGING ACCIDENT
CCNTV6
7.5K views

1:50:59
Logging Towards The Cloudline
Scene Drop
824 views

42:27
PyCon PT 24 | Better logging in Python
PyCon Portugal
345 views

3:41
Delhi Gurugram Water Logging Problem In Metro Cities Explained | RainWater Drainage System | Boldsky
Boldsky
802 views

1:36
Government-contracted loggers underestimate the number of endangered greater gliders in areas set for logging
ABC NEWS (Australia)
307 views

4:10
Difference between Computationally Secure and Unconditional Secure Cipher | Information Security
Easy Engineering Classes
6.4K views
![Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]](/image/i.ytimg.com/vi/Hs-7ixoSqAA/xhqdefault.jpg.pagespeed.ic.BPwrxXKFrf.jpg)
41:29
Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]
Microsoft Research
77 views

0:13
Difference between unconditionally secure and computationally secure in cryptography and .....
SUKANYA BASU
973 views
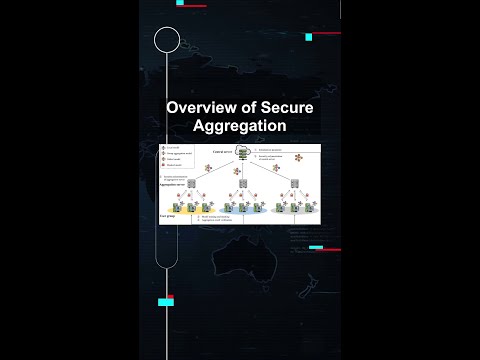
0:55
Overview of Secure Aggregation #ai #artificialintelligence #machinelearning #aiagent Overview Secure
NextGen AI Explorer
12 views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

0:05
Read Secure Software and Comm. on Handheld Devices: Secure Software and Communication on Handheld
Isaksen
2 views

2:05
Secure USB Flash Drive - SanDisk Enterprise Secure ...
John Objet
1 views

4:53
Best browser for privacy 2021 | Iridium Browser | A browser securing your privacy | Most Secure Web Browsers That Protect Your Privacy | most secure browser 2021
FOCUS EXCLUSIVE
13 views

46:18
Roll Your Own Secure Cloud Storage with SSHFS - Secure Shell File System - Hak5
Hak5
5 views

3:39
Medical Coding Services | Secure Medical Coding & Secure Medical Data Handling
PDNSeek .com
5 views

0:25
A Secure Erasure Code-Based Cloud Storage System with Secure Data Forwarding
satish20059
259 views
4:17
Improved Eaack Develop Secure Intrusion Detection System For Manets Using Hybrid Cryptography
1 Crore Projects
37 views

19:03
What is SSL? | What is SSL Ceritificate? | SSL Architecture and Protocols | Secure Socket Layer
Chirag Bhalodia
72.1K views

10:05
Secure IoT Messaging with Symmetric Keys: A Simplified Guide
LEARNACON
79 views

5:49
US Marines Still Battling to Secure Fallujah 2004
Channel 4 News
2.2M views

55:35
Cryptography and Network Security Part 4/5 | WIlliam Stallings |Secure communication - S8 EC, CS,KTU
bushara abdulrahim
498 views
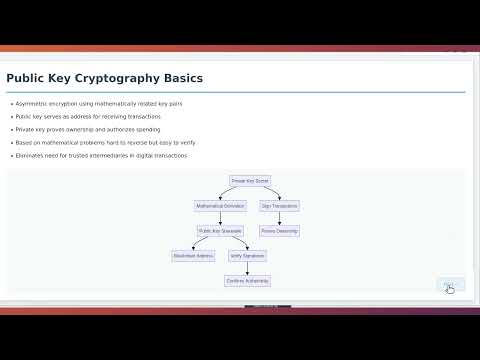
44:23
Blockchain Cryptography Math Explained: A Guide to the Mathematics Behind Secure Digital Ledgers
Network Technician
6 views
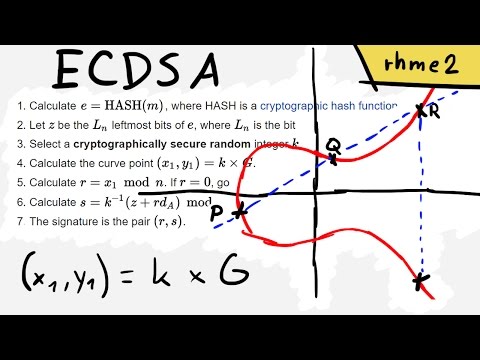
8:19
Breaking ECDSA (Elliptic Curve Cryptography) - rhme2 Secure Filesystem v1.92r1 (crypto 150)
LiveOverflow
78.4K views

28:17
Parte 1 - Introdução ao Algoritmo SHA 256 - Secure Hash Algorithm SHA256
Laboratório de Inutilidade Pública
7.2K views

0:16
Wireless network secure encryption protocol #networksecurity
cyberninja
206 views
36:07
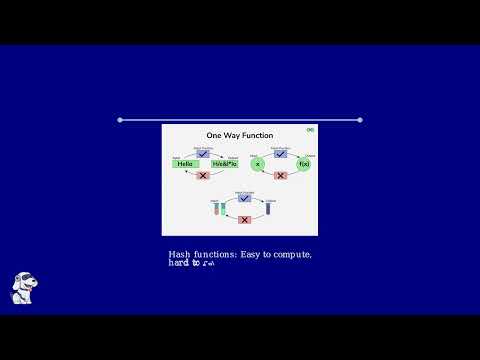
Quantum Cryptography: How Weird Physics Could Secure Your Secrets Forever
Volkan Duran
55 views

10:22
INFORMATION SECURITY( HINDI).WHAT IS CRYPTOGRAPHY AND HOW IT WORKS TO SECURE YOUR INFORMATION.(ICT)
Computerprime
2.3K views

6:17
Secure QR-Code Based Message Sharing System Using Cryptography and Steganography
SHOAIB SHAIKH
633 views

0:35
Cracking The Code - Exploring Secure Hash Algorithms - SHA Short #cybersecurity #hashing
Technically U
1.1K views

5:31
#54 S/MIME - Secure MIME protocol - Functions, Services |CNS|
Trouble- Free
215.2K views

0:09
Why Sleep Training Might Disrupt Secure Attachment | Gentle Parenting Insights
Shalee Bayne | Wellness & Honest Motherhood
100.1K views

7:41
An RSA-Based Secure Image Steganography Technique Using Adaptive Data Hiding - Mid
Akash Joy
7 views
19:53
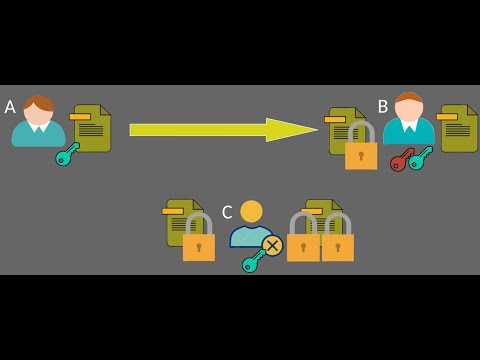
Understanding Asymmetric Encryption: The Key to Secure Communication
Visualize Byte Code
9 views
12:01
Secure Data Transfer Based on Visual Cryptography - Part1
AmAn
30 views

14:53
Quantum Cryptography: The Future of Secure Communication
CyberSecTV
32 views

0:42
Unlocking the Quantum Internet Future of Secure Communication #quantumInternet #securecommunication
Inspiration Station
11 views

3:59
The Lava Lamps That Help Keep The Internet Secure
Tom Scott
4.2M views
12:54
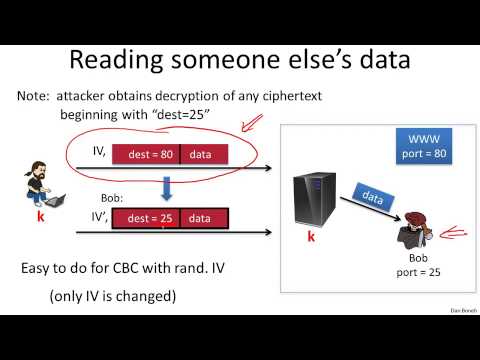
7 1 Active attacks on CPA secure encryption 13 min
Jake Danniel
305 views
3:17
How Does No-Cloning Theorem Secure Quantum Cryptography? - Quantum Tech Explained
Quantum Tech Explained
0 views

32:28
17-How Public Key Distribution Works? 💡 | Secure Key Sharing in Network Security
Sundeep Saradhi Kanthety
107.5K views