Search Results for "Cryptographic Firewalls"
Find videos related to your search query. Browse through our collection of videos matching "Cryptographic Firewalls". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Cryptographic Firewalls"
50 results found
6:53
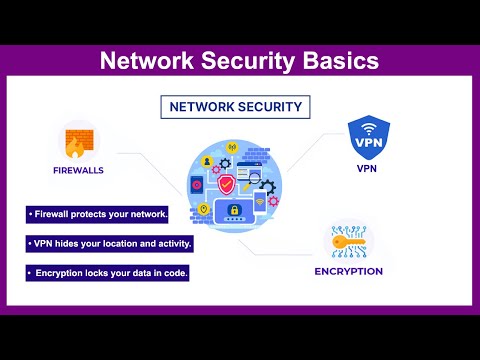
Network Security Basics | Firewalls, VPNs, & Encryption | In Hindi |
Explore - The Knowledge Tv
460 views

9:22
Cryptography & Firewalls Explained | Symmetric vs Asymmetric Keys, Packet Filtering, Proxy | English
CSE Gawd
3 views
14:09
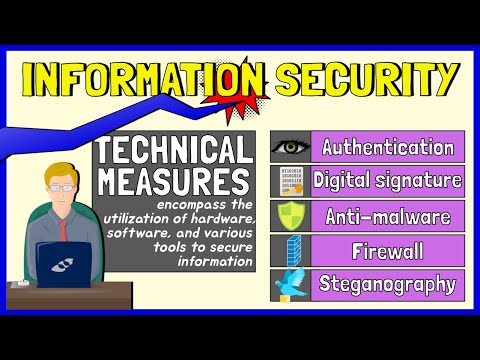
Information Security Measures (Authentication, Digital Signature, Firewalls, Steganography)
5-Minute Lessons by Victor
973 views

17:38
Cryptography & Firewalls Explained | Symmetric vs Asymmetric Encryption, Packet Filtering & Proxy
CSE Gawd
4 views

5:39
What Is Firewall ? | Firewall Explained | Firewalls and Network Security | Simplilearn
Simplilearn
438.4K views

9:15
Wie funktionieren Firewalls? | Fachinformatiker Prüfungsvorbereitung IHK
Pixel Insider
32.4K views
0:39
Rhadamanthys Stealer: How PNG Steganography Evades Firewalls to Steal Your Data
Hacked dAily
167 views

36:01
Firewalls | Cryptography and System Security
Ekeeda
96 views

13:45
Lec-85: What is Firewalls and How it Works | Packet Filtering firewall explained in Hindi Part-1
Gate Smashers
820.3K views
12:29
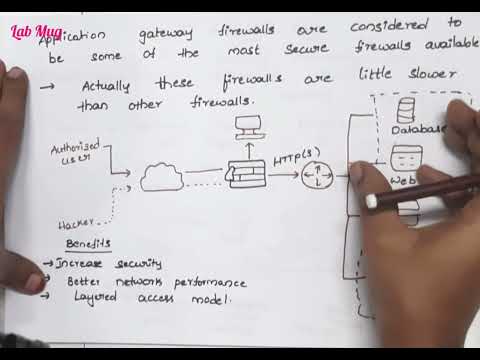
Firewall and types of firewalls in cryptography and security #networking #cryptography
Lab Mug
4.2K views
1:20
Snowden firewalls US-Russia talks
TIMES NOW
203 views
14:46
Firewalls and Computer Network Security, Hindi Urdu Networking tutorials for beginners
Ifactner
3 views

9:48
Firewalls And Their Uses
Social Frontier
11 views

2:44
YTP - RARs, Firewalls & Automobiles
Ukfwhitwell
21 views

13:30
Firewalls-Generations-and-Network-security-Computer-Networking-tutorial
Riaz Hussain
48 views
![[PDF Download] Practical Firewalls (Practical) [Download] Full Ebook](/image/s1.dmcdn.net/v/DOTKP1e0mVggk2UUE/x720)
0:06
[PDF Download] Practical Firewalls (Practical) [Download] Full Ebook
Elsater
1 views

0:29
Download Network Security Firewalls And VPNs Read Online
RandalRodolfoRoysden
2 views

0:06
Read Guide to Firewalls and Network Security: Intrusion Detection and VPNs PDF Online
Sbjorn
1 views

0:05
Read Guide to Firewalls and Network Security PDF Free
Irene Bonde
3 views

6:19
010-Network Devices-Firewalls
Ahmed Salama Academy
16 views

10:55
Firewalls and its types in Cryptography
The viral zone
2 views
4:09
Managing your firewalls with McAfee Firewall Profiler
David Strom
84 views
11:47
Types of Firewalls-Stateful Inspection-Application Proxy-Circuit Proxy(KTU CSE 409 Cryptography)
KTU Computer Science Tutorials
8.3K views

8:50
Introduction to Cryptographic Attacks | Types of Cryptographic Attacks Explained With Measures
Shree Learning Academy
2.3K views

0:34
How To Pronounce Cryptographic🌈🌈🌈🌈🌈🌈Pronunciation Of Cryptographic
Isabella Saying
33 views

0:34
Cryptographic | CRYPTOGRAPHIC meaning
Word Mastery Channel
0 views

0:02
How to pronounce Cryptographic / Cryptographic pronunciation
Raccoon Teaches You
48 views

9:59
VTU June 19 - Definition And Properties of Cryptographic Hash - Cryptographic And Network Security
Education
66 views

6:55
Attacks on Cryptographic Hash Algorithms || what is cryptographic? || Best Mind Like
Best Mind Like
45 views

0:33
How Cryptographic Hash Functions Keep You Safe! 🔍 #cryptocurrency #bitcoin #blockchain #shorts
Cryptocurrency Classroom
94 views
2:24
OWASP TOP 10 - Sensitive Data Exposure / Cryptographic failures
WhiteHats
3.2K views

23:38
The Price Of Active Security In Cryptographic Protocols
Fidelity Center for Applied Technology (FCAT®)
31 views

6:31:26
Cryptographic Ledger Database, Analysis & Applications in Decentralized Blockchain & Financial World
HKEBA
71 views

37:26
A complete overview of SSL/TLS and its cryptographic system
TECH SCHOOL
136.0K views

16:03
A Cryptographic Implementation: Hybrid Encryption
Luciano Scarpaci
25 views

12:21
Rapid Prototyping of Cryptographic Systems on Chip - By Dr. Issam W. Damaj
Dr. Issam Damaj
68 views

0:31
CS8792 / Cryptographic and network security / Unit -3 (30 MCQ ) important Questions with answers..
Lincy's Style
416 views

29:55
Cryptographic hash function: Introduction
Introduction to Cryptology
3.7K views

6:06
Unplugged: The show. Part 8: Cryptographic protocols
UC Computer Science Education
14.4K views

0:47
The Enigma Machine: Cryptographic Innovator
Bored Sapien
318 views
7:57
griet-it-2012- a cryptographic technique for heterogenous sensor networks.wmv
Maruti Kumar
18 views

0:58
The Secret Codes of the Enigma Machine: Cryptographic Turning Point
History with AI
263 views

11:58
SSProve: A Foundational Framework for Modular Cryptographic Proofs in Coq (CSF 2021)
Philipp Haselwarter
44 views
17:31
BIKE - Cryptographic Engineering
Danny Silvestre Suarez
243 views

6:03
Cryptanalysis - Cryptographic Services - Network Security - CCNA - KevTechify | vid 63
Kev Techify
221 views

1:38:51
PETS 2022 Moti Yung Keynote Privacy Integrated Computing” Cryptographic Protocols in Practice
All Hacking Cons
17 views

10:14
Bitcoin - Cryptographic hash function
Khan Academy
284.5K views

1:05
The Science of Blockchain: Cryptographic Trust
Thought Shot
190 views
4:06
62 CISSP 2015 D01 S18 T01 STEP Cryptographic Lifecycle
PanZa PanZa
1 views
7:34
ITS 122 - 3.1 Cryptographic Principles
John Johnson
6 views
Page 1