Search Results for "secure AI"
Find videos related to your search query. Browse through our collection of videos matching "secure AI". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "secure AI"
50 results found
13:28
Secure Data Transfer Based on Visual Cryptography- Working Demo
AmAn
121 views
10:54
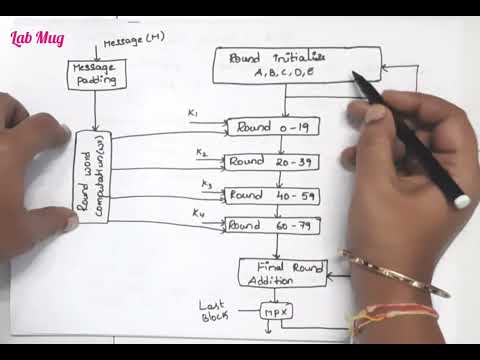
Secure Hash Algorithm (SHA) in Cryptography and Network Security #cryptography #networking #security
Lab Mug
11.2K views
14:03
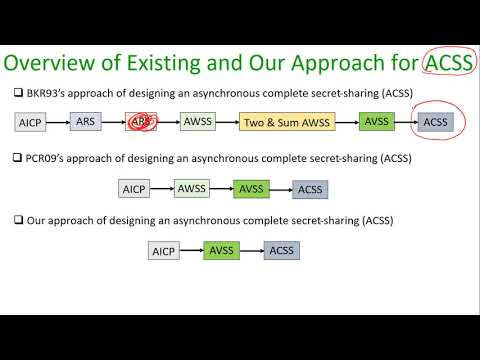
Brief Announcement: Optimally-resilient Unconditionally-secure Asynchronous Multi-party Computation…
PODC–DISC
55 views
0:11
Cryptography for Secure Communications: RSA
KD Sec n Tech
14 views

19:53
67 Kid vs Most Secure House in Minecraft!
Dash
40.8K views

0:40
Unlocking cryptography to secure your data. AES,RSA,SHA, and MD5
MossB Network
167 views

26:32
Breaking the Circuit Size Barrier for Secure Computation Under DDH
IACR
865 views

3:42
Hybrid Cryptography Algorithm For Secure And Low Cost Communication | IEEE Major Projects | B-Tech
Cloud Technologies
65 views

3:15
How Does The BB84 Protocol Secure Quantum Communications? - Quantum Tech Explained
Quantum Tech Explained
13 views
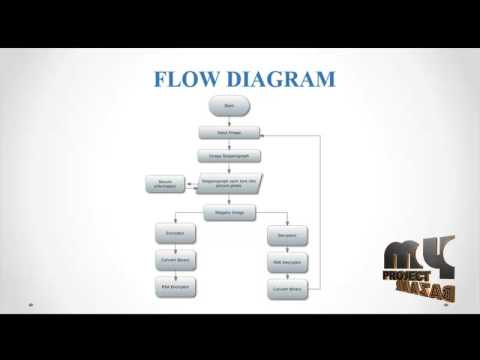
5:13
Secure Binary Image Steganography Based on Minimizing the Distortion on the Texture
MyProjectBazaar
36 views

0:41
🔐 IKE Authentication Explained Secure Cisco VPN | IPsec & Pre Shared Key Step by Step #ccnpsecurity
CoreSah Networks
212 views

0:30
Cryptography in Blockchain: Keeping Things Secure and Real
Éric Bégin
3 views
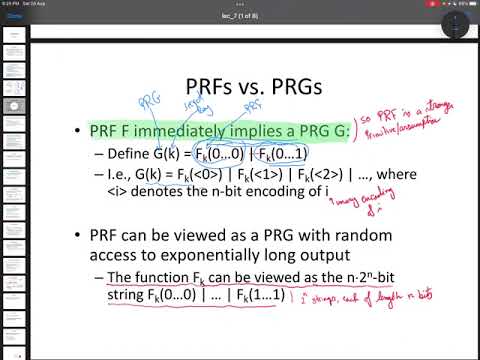
50:22
Lecture 11: Encryption scheme that is CPA-secure
Cryptography - علم التشفير
773 views

1:30
Protesters demand a deal to secure the release of Israeli hostages
Sky News
10.6K views

0:40
RSA: Secure Key to Modern Cybersecurity #cybersecurity #cryptography #cybersecurityeducation
SimplyCompute
142 views

1:56
Cryptography project - Secure your passwords using python
Christeen T Jose
815 views
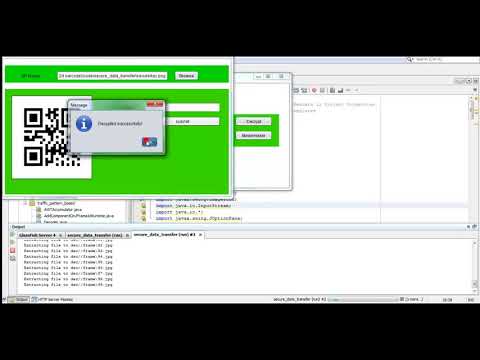
3:24
Secure Data Transfer Video Steganography Projects | Student Projects
Python Projects
475 views

9:51
Cryptography in Blockchain 🔐 | Secret Behind Secure Transactions Explained in Hindi | Day 3
HeatCode
0 views

0:34
India's Quantum Leap! 🇮🇳🔐 QKD system for secure telecom is HERE! #viral #shorts #quantum
Gettobyte
1.5K views

4:01
Speech Steganography | Data Hiding in Speech | Secure Speech File using Arduino or Raspberry-Pi
Techpacs
193 views

4:27
How Secure Is Distributed Computing? - Next LVL Programming
NextLVLProgramming
3 views
10:21
SHA: Secure Hashing Algorithm - Computerphile
Computerphile
1.3M views

7:09
Proofs in Cryptography Lecture 12 ROM Construction Example CPA secure RSA Encryption
Science Traveller
269 views

1:10:14
Chapter 13: Secure Processor Architectures (Part I) -- Cryptographic Fundamentals and Encryption
Smruti R. Sarangi
467 views

0:59
3 ways the 5D mystic functional adult enlightenment person knows secure attachment in the body-mind
Inspiring Human Potential
26 views

0:58
"The Most Secure Method Are Telegram And WhatsApp" Bryce Case Jr - Shawn Ryan Show
Armed Sphere
39.2K views

17:54
Episode 4 | Advanced Cryptography: PKI, Digital Certificates & Secure Protocols | BCIS 4345
Joseph H.Schuessler
49 views
17:01
Steganography secure information passing sys C# asp.net Sql Server Web Project | asp208 #highblixasp
Highblix
378 views
14:34
How to Secure Switch from unauthorized access
Dipak Bari
3.2K views

11:23
Il tuo PC ti protegge ancor prima del login: Secure Boot & TPM spiegati
CinnamonSec
247 views
6:09
AES ALGORITHM BASED SECURE DISCRETE WAVELET TRANSFORM STEGANOGRAPHIC TECHNIQUE FOR THE IMAGES
VERILOG COURSE TEAM
739 views

3:01
Why Is Public-key Cryptography Crucial For Secure Communication? - Emerging Tech Insider
Emerging Tech Insider
0 views

0:57
Is Any of Your Data Really Secure?
Neural Vibrations
280 views

2:12
Secure Large File Transfer
NeoCertified
159 views

2:37
Distributed Programming Fullstack 2021 | S3P20 | Security | Intro Creating a Secure Frontend
Lars Bilde
162 views

1:35:57
Cryptography and Network Security Part 1/5 | WIlliam Stallings | Secure communication - S8 EC KTU
bushara abdulrahim
1.3K views

1:00
How A Solo-Polyamory Secure Attachment 5D Mystic Enlightenment Woo-Woo-Pseudoscience Woman Sees Love
Inspiring Human Potential
31 views
8:55
Final Year Projects | Secure Data Hiding Algorithm using Encrypted Screte Message
ClickMyProject
2.3K views
6:09
Symmetric vs Asymmetric Encryption Explained 🔥 | The Secret Math Behind Secure Communication!
Escoding
506 views

0:35
How Does Cryptography Secure Blockchain Networks
Visiion io
10 views

6:05
Secure Pixel Secrecy Embedding Secret Keys with Python and LSB Steganography in Images
1Crore Projects
4 views

25:25
I Built The SMALLEST SECURE BASE In 99 Nights In The Forest!
Grave
52.4K views
21:55
On the Communication required for Unconditionally Secure Multiplication
IACR
399 views

45:14
PQShield Webinar: Secure Messaging in a Post-Quantum World
PQShield
3.4K views

5:10
Crypto audit to enforce authorized encryption standards - Cisco Secure Network Analytics
Cisco Secure Network Analytics
389 views

2:11
Secure Medical Imaging Data using Cryptography | Classification |Brain Tumor Dataset | MATLAB | FYP
Saqqiya Technology Point
170 views
10:40
SecRBAC: Secure data in the Clouds ||best ieee 2017 java projects list.
SD Pro Solutions Pvt Ltd
194 views

0:11
Encryption method commonly used to secure wireless networks?#securewireless#sciencefather#research
Popular Engineer Research
65 views
0:16
Mastering Cryptography Secrets of Secure Messaging
CyberSecurity Summary
24 views

5:24
Final Year Projects | A Secure Image Based Steganographic Model Using RSA Algorithm and LSB I
ClickMyProject
7.0K views
Previous Page 4