Search Results for "less secure hashing technique"
Find videos related to your search query. Browse through our collection of videos matching "less secure hashing technique". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "less secure hashing technique"
50 results found

0:35
Hashing vs Encryption 🔐 #hashing #encryption
Neszen
381 views

5:03
Trent Kelly Asks General Point Blank: Is Our ‘Southern Border More Or Less Secure Today?’
Forbes Breaking News
2.5K views

39:28
Hashing Technique by Mr. Akhilesh Kumar Srivastava
CETL at ABES Engineering College
2.0K views
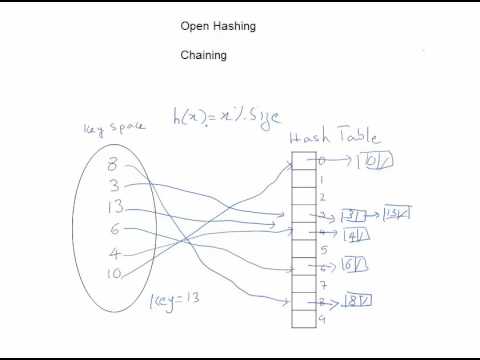
17:04
Hashing Technique - Simplified
Abdul Bari
847.6K views

0:35
Cracking The Code - Exploring Secure Hash Algorithms - SHA Short #cybersecurity #hashing
Technically U
1.1K views
10:21
SHA: Secure Hashing Algorithm - Computerphile
Computerphile
1.3M views

14:19
Asymmetric Algorithms & Hashing Explained Simply | CRISC Domain 4 | Secure Data & Digital Signatures
ISACA PREP ACADEMY
66 views

3:01
What Is Hashing And How Does It Make Crypto Passwords Secure? - All About Crypto Exchanges
All About Crypto Exchanges
0 views
0:40
HASHING KEY TO SECURE PASSWORD
TechHub
154 views

0:11
Cryptography techniques || Substitutional technique || Transpositional technique || UNIT 01
Online Learning
5.0K views
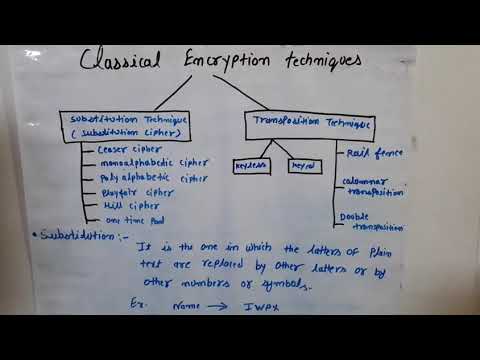
4:05
Classical encryptiin techniques, substitution technique, transposition technique
Gaurav Khatri
498 views

23:16
NIS-3.2-1 : Types of Cipher Technique (Substitution Cipher Technique, Caesar cipher)
rathod_sir
361 views

4:05
Substitution Cipher Technique V/s Transposition Cipher Technique in Cryptography and Network Securit
Short Tricks Learning
631 views

0:46
What technique do you use during competitive eating?: Competitive Eating Strategy And Technique
Scribble
1 views

5:42
Hair Cutting Technique: Mahogany Cutting Technique
Grant Sharp
8.7K views

7:41
An RSA-Based Secure Image Steganography Technique Using Adaptive Data Hiding - Mid
Akash Joy
7 views
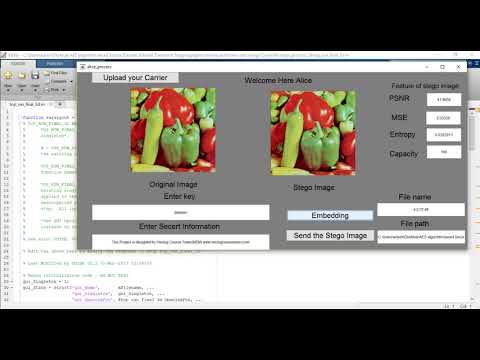
6:09
AES ALGORITHM BASED SECURE DISCRETE WAVELET TRANSFORM STEGANOGRAPHIC TECHNIQUE FOR THE IMAGES
VERILOG COURSE TEAM
739 views

10:38
SECURE DISCRETE WAVELET TRANSFORM STEGANOGRAPHIC TECHNIQUE FOR THE COLOR IMAGE
VERILOG COURSE TEAM
1.3K views
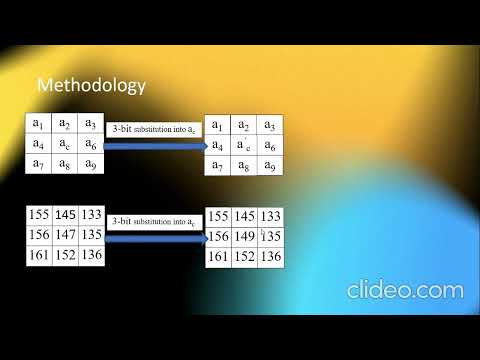
11:10
An RSA-Based Secure Image Steganography Technique Using Adaptive Data Hiding - Final
Akash Joy
22 views
5:28
Secure Data Aggregation Technique for Wireless Sensor Networks in the Presence of Collusion Attacks
MyProjectBazaar
18 views
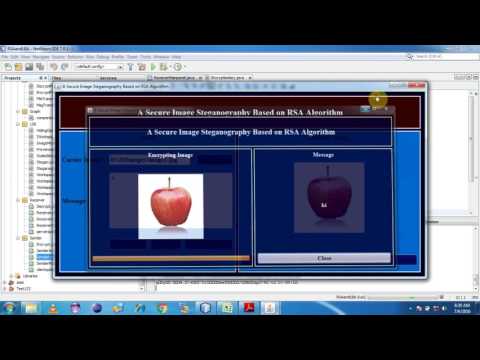
1:45
A Secure Image Steganography Based on RSA Algorithm and Hash LSB Technique
InnovationAdsOfIndia
3.9K views

4:03
A SECURE IMAGE STEGANOGRAPHY BASED ON RSA ALGORITHM AND HASH-LSB TECHNIQUE
VERILOG COURSE TEAM-MATLAB PROJECT
464 views
7:22
IMPROVING PIXEL CLARITY AND SECURE DATA TRANSFER IN VISUAL CRYPTOGRAPHY TECHNIQUE
Gopiram Rameshkumar
90 views
5:05
Secure Image Encryption Technique Using Matlab #steganography #mail #finalyearprojects
Amodha InfoTech
34 views

4:10
Difference between Computationally Secure and Unconditional Secure Cipher | Information Security
Easy Engineering Classes
6.4K views
![Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]](/image/i.ytimg.com/vi/Hs-7ixoSqAA/hqdefault.jpg)
41:29
Towards more Practical Secure Computation: Efficient Protocols for Secure Linear Algebra [1/2]
Microsoft Research
77 views

0:13
Difference between unconditionally secure and computationally secure in cryptography and .....
SUKANYA BASU
973 views
0:55
Overview of Secure Aggregation #ai #artificialintelligence #machinelearning #aiagent Overview Secure
NextGen AI Explorer
12 views

8:37
SSH (Secure shell) protocol in Hindi | Secure shell protocol in Network Security
Abhishek Sharma
84.3K views

0:05
Read Secure Software and Comm. on Handheld Devices: Secure Software and Communication on Handheld
Isaksen
2 views

2:05
Secure USB Flash Drive - SanDisk Enterprise Secure ...
John Objet
1 views

4:53
Best browser for privacy 2021 | Iridium Browser | A browser securing your privacy | Most Secure Web Browsers That Protect Your Privacy | most secure browser 2021
FOCUS EXCLUSIVE
13 views

46:18
Roll Your Own Secure Cloud Storage with SSHFS - Secure Shell File System - Hak5
Hak5
5 views

3:39
Medical Coding Services | Secure Medical Coding & Secure Medical Data Handling
PDNSeek .com
5 views

0:25
A Secure Erasure Code-Based Cloud Storage System with Secure Data Forwarding
satish20059
259 views

2:17
Math in 5 Minutes (More or Less), Part 8: Public Key Cryptography
Math Beyond Zeno of Elea
4.6K views

4:54
How to Hide Secrets Inside Images in Less Than 5 Minutes
Dinjik
1.9K views
1:42:08
Learn Quantum Cryptography (#3 of 3 series): Less certainty, more security -- Meetup-Lite 20200826
Harrisburg Quantum
77 views

3:38
Tame Impala - The Less I Know The Better (Audio)
tameimpalaVEVO
245.7M views
![T. Less - Hideg (feat. Xiaoling) [Official Music Video]](/image/i.ytimg.com/vi/3bmTENeHfLI/hqdefault.jpg)
3:26
T. Less - Hideg (feat. Xiaoling) [Official Music Video]
T. LESS
52.1K views

1:12
A hat trick in less than 10 minutes. Take a bow, Ludmila. #nwsl
National Women's Soccer League
311.8K views

3:47
Greater Than Less Than Song for Kids | Comparing Numbers to 1000
Math Songs by NUMBEROCK
6.0M views

0:20
Mercy less Killers ☠️
AJ EDITZ
8.7M views

0:30
How Real Betis signed Antony permanently from United for €75 million less than his price.😳😰
BallBlitz
1.2M views

0:39
Breaking encryption with 100x less qubits? #quantumcomputing #encryption #security
Anastasia Marchenkova
15.8K views

0:33
Mathematics Addition Trick - Reverse Addition | Add any numbers in less than 2 Seconds #Shorts
Agyaan Tech
1.0K views

1:24
Session Hijacking Explained in less than 90 Seconds #SessionHijacking #Cybersecurity #EthicalHacking
Yaniv Hoffman
5.5K views
23:38
Bootstrapping fully homomorphic encryption over the integers in less than one second
IACR
1.3K views

1:02
How Israel could defeat Egypt in less than a day
StrikePoint
1.8M views
6:26
Dividing any number by 9 in less than 5 seconds | Math Tips and Tricks
Akash Vukoti
323.9K views