Search Results for "key escrow information security"
Find videos related to your search query. Browse through our collection of videos matching "key escrow information security". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "key escrow information security"
50 results found

3:55
difference between public key and private key, what is public key and private key, o level exam,
tech MCQ & theory
3.4K views

2:55
The difference between Private key and public Key || Symmetric key and Asymmetric key cryptography
Pooja Patel
10 views

3:11
Public key vs Private key ll Symmetric key vs Asymmetric key
Guptasmartclasses
38 views

6:57
Key Management and Key Distribution in Cryptography | Key Management | Key Distribution
Chirag Bhalodia
100.9K views

0:48
°FIFA 14° °KEYGEN°°KEY GENERATOR°°ACTIVATION°°PRODUCT KEY°°SERIAL KEY°°LICENCE KEY
morientesmalaka
241 views

3:17
Best Key West Restaurants | Best Key West Nightclubs | Best Key West DJs | Whats Hot Key West
LJ Cange
1 views

1:10
Magic Key Extractor Key Gen (Magic Key Extractormagic key extractor 2015)
Brenda Diaz
27 views
![Mirrakey License Key Generator Key Gen [Mirrakey License Key Generatormirrakey license key generator 2015]](/image/s2.dmcdn.net/v/8_ZGQ1e0GZW5oh8l_/xx720.pagespeed.ic.P1ZMrUV2OK.jpg)
1:50
Mirrakey License Key Generator Key Gen [Mirrakey License Key Generatormirrakey license key generator 2015]
Bob Sanderson
6 views

1:00
Key locksmith Dubai, key repairing, key making, key locksmith, locksmith Dubai
Ummeammarah11
2 views

18:08
CS14: Digital Signature in Cyber Security | Symmetric Key | Asymmetric Key| Public Key Cryptography
University Academy
37.2K views

6:55
Key Distribution in Symmetric key |Symmetric key Distribution |Network security Hindi...
DK Technical Point 2.0
3.1K views

7:56
Key Distribution in Asymmetric Key |Asymmetric key distribution |Network Security Hindi explain
DK Technical Point 2.0
1.1K views

6:43
Network & Cyber Security Lecture: Symmetric key Encryption (Private Key) Key Based Cryptography
Sanjay Pathak
1.8K views

2:04
symmetric key and asymmetric key in network security ⚡| cyber security class in hindi | sampat sir
Anvira Education
271 views

1:59
★KASPERSKY INTERNET SECURITY KEY - KASPERSKY INTERNET SECURITY 2017 SERIAL KEY ACTIVATION★
Mixcraft 8 Activation Key 2017 Full Crack
347 views

8:01
Web Security-Security Threats and their solution in hindi-Security Policy-computer network security
Unbeaten Learning
77.8K views

0:36
mandurah security system, home cctv security systems mandurah, cctv security systems mandurah, mandurah security systems, cctv system mandurah
lockdownse
1 views

1:16:27
Information Security—Before & After Public-Key Cryptography
Computer History Museum
112.2K views

3:21
KDC (Key Distribution Center): KDC in information security |KDC in cryptography in hindi | Hindi
Zixplain
9.1K views

5:19
15 Public Key Cryptography ISACA CISM DOMAIN 3 INFORMATION SECURITY PROGRAM
TUTORIAL
10 views

7:42
Symmetric Key Cryptography ll Information and Cyber Security Course Explained in Hindi
5 Minutes Engineering
264.3K views
6:02
Trapdoor Function in Asymmetric Key Cryptography - | Information Security Lectures Hindi
Easy Engineering Classes
7.4K views
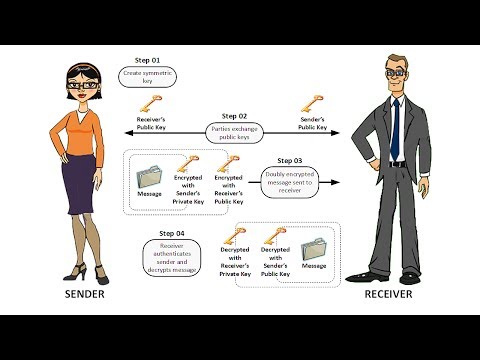
28:15
Data Interception and Public Key Encryption - Information Security Lesson #9 of 12
Dr. Daniel Soper
28.9K views

9:01
#15 Symmetric & Asymmetric Key Cryptography With Diagram |Information Security|
Trouble- Free
52.7K views
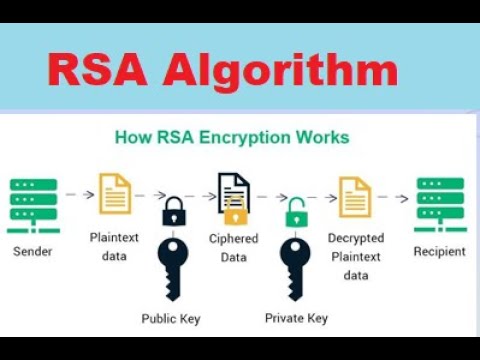
11:12
RSA Algorithm in Information Security | Public Key Cryptography: RSA Encryption Algorithm | RSA
Tech CS&IT
266 views

11:52
Information & Network Security Lecture -- Key Distribution Techniques | public-secret | (Eng-Hindi)
Well Academy
54.2K views

8:21
key distribution problem in cryptography information security and IT LAWS
CSJM CLASSES INSTRUCTOR RAM SWAROOP
1.1K views
7:43
Symmetric Key Cryptography | Information security | eVeda
eVeda
54 views
9:31
Information Security | Vigenere cipher Solved example | Encryption | Decryption | How we Find key ?
NextGen Learners
13 views

0:05
Read Access Control Authentication And Public Key Infrastructure (Information Systems Security
Tuuli Mark
1 views

0:08
Read Access Control Authentication And Public Key Infrastructure (Information Systems Security
Thierse
0 views

0:05
Download Access Control Authentication And Public Key Infrastructure (Information Systems Security
Maisi Baker
2 views

0:26
Read Multivariate Public Key Cryptosystems (Advances in Information Security) Ebook Free
Nicole Willis
0 views

9:06
Asymmetric Key Cryptography ll Information and Cyber Security Course Explained in Hindi
5 Minutes Engineering
216.9K views
19:03
Lec-38_ Key Distribution Scenario|Information Security|Computer Engineering
Computer_IT_ICT Engineering Department : LJIET
1.2K views
14:16
Information Security | Vigenere Cipher | cryptanalysis | How we find Key length From Ciphertext
NextGen Learners
50 views

0:44
Cryptography and information security: encryption algorithms and methods for ensuring data security.
Superpupt
75 views

12:03
VIGENERE CIPHER LESSON 7 |Polyalphabetic cipher|Cryptography& network security| Information security
Shashi KS
94 views

6:58
Vigenere cipher in easy | huzu's tution | Information Security | cyber security #education #cipher
Cyber Geek
148 views

7:31
Basics Of Network Security ll Information and Cyber Security Course Explained in Hindi
5 Minutes Engineering
288.9K views

9:26
Security Policy ll Information And Cyber Security Course Explained in Hindi
5 Minutes Engineering
252.4K views

14:25
#3 Types Of Security Attacks- Active & Passive Attacks and their Types |Information Security|
Trouble- Free
105.8K views

1:09
12 Security Technologies & Controls ISACA CISM DOMAIN 3 INFORMATION SECURITY PROGRAM
TUTORIAL
330 views
8:15
playfair cipher in network Security | Information Security | Cryptography
Techystudy Best Learning Online
109 views

0:30
counter mode- Decryption | information security | cyber security #studyeasierbypoojapatel
Pooja Patel
106 views
1:25:42
8 - Information Security - Continue Cryptography - Cloud & Azure - Physical Security (Arabic)
Madeeh Nayer
161 views

11:23
USENIX Security '21 - A Large-Scale Interview Study on Information Security in and Attacks...
USENIX
240 views

1:31
Symmetric cipher model in Hindi || Information Security and Cyber Security || Study easier by Pooja
Pooja Patel
126 views

11:28
Information Security || Security Attacks | In Urdu
Computer Tech
40 views

1:26
Network Security UNIT 1 Topic 1/4 Information Security
DIWAKAR TIWARY
256 views