Search Results for "ai vs ml vs dl example"
Find videos related to your search query. Browse through our collection of videos matching "ai vs ml vs dl example". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "ai vs ml vs dl example"
50 results found
15:56
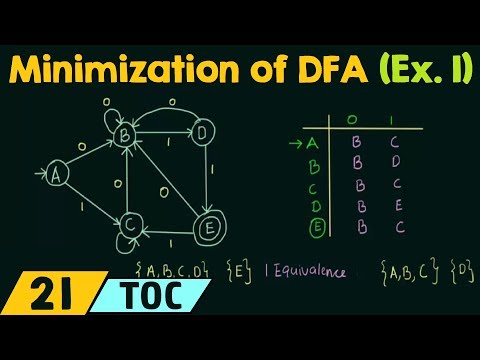
Minimization of DFA (Example 1)
Neso Academy
2.0M views

2:46
Example 6: Factoring quadratics with two variables | Algebra I | Khan Academy
Khan Academy
213.5K views

3:45
RSA Asymmetric Encryption and Signing with Public Private Keys - Usecases with Example
Techno Saviour
4.7K views

8:01
FA to RE Conversion by State Elimination Method | Example
Learn with ART
101 views

4:20
Factoring quadratics as (x+a)(x+b) (example 2) | Mathematics II | High School Math | Khan Academy
Khan Academy
778.6K views
20:05
3.1.3 Example of Turing Machine as an Adder | TOC | Unit - 3 | IPU
Collate
731 views

14:53
Principles Of Public key Cryptography or Asymmetric Key Cryptography with example #cns #jntuh #feed
Concept Clear
191 views
7:51
3. Space Complexity Of Algorithms with Example - Calculating Space Complexity |DAA|
Trouble- Free
123.3K views

28:50
Big Oh(O) vs Big Omega(Ω) vs Big Theta(θ) notations | Asymptotic Analysis of Algorithms with Example
Simple Snippets
230.4K views

17:48
Lec 17: Preemptive Priority Scheduling Algorithm in OS with example | Operating System
Jenny's Lectures CS IT
548.3K views
7:36
Minimization using K-Map explained with example !!!
Nimish Munishwar
18 views

21:36
What is Public Key Infrastructure | Working of PKI | Real time example of PKI
Chirag Bhalodia
38.5K views
12:59
Caesar Cipher Encryption and Decryption with Solved Example || Substitution Technique
A Z Computing
37.3K views
13:10
Logistic Regression Algorithm in Machine Learning with Solved Numerical Example by Mahesh Huddar
Mahesh Huddar
172.7K views

7:04
Theory OF Computing | Nfa to Dfa Conversion Example 2
BD Top Education
74 views
11:21
Deterministic Finite Automata (Example 2)
Neso Academy
1.4M views

5:31
Vigenere cipher with example | cryptography
Learn Math
74 views
11:42
2. Hill Cipher Solved Example 3x3 Key Matrix | Hill Cipher Encryption and Decryption Mahesh Huddar
Mahesh Huddar
27.0K views

2:20
Vigenere cipher|Vigenere cipher encryption and decryption|Vigenere cipher example
Atiya Kazi
684 views

4:13
Monoalphabetic Substitution Cipher explained step by step with example !!!
Nimish Munishwar
16.2K views

8:51
Hill Cipher Decryption in 5 steps Example in hindi | Information and Network Security Course | GTU
AXL huB
200 views

10:05
RSA Example Lecture 1 | p=7, q=11, plaintext=m=9, Find public key (e), private key (d) & ciphertext
TRN CSE Tutorials
2.2K views

0:41
Euclidean algorithm example
Michael Penn
9.9K views

7:43
Applied Cryptography: Caesar Cipher Example 1 (3/3)
Leandro Junes
1.1K views

6:27
Regular Languages Closed Under Suffix Example
Easy Theory
934 views

14:21
A* algorithm in AI (artificial intelligence) with example || A Star algorithm || Informed search
Sudhakar Atchala
73.2K views
44:01
Simplified Data Encryption Standard (DES) Example
Steven Gordon
74.5K views

16:50
REAL LIFE example!! (TCP/IP and OSI layers) // FREE CCNA // EP 4
NetworkChuck
969.4K views

49:50
Substitution Ciphers : Additive and Multiplicative Ciphers with Example in Bangla | Caesar Cipher
Jahidul Islam GUB
1.3K views
13:04
Palindrome using Turing Machines | Problems on Turing Machines|Example 5| Theory of Computer Science
Sridhar Iyer
1.8K views
0:27
Anderson Cooper, 4K Original/(Deep)Fake Example
LipSynthesis
570.0K views
15:20
Math 574, Lesson 2-3: Turing machines - an example
Jan Reimann
2.5K views
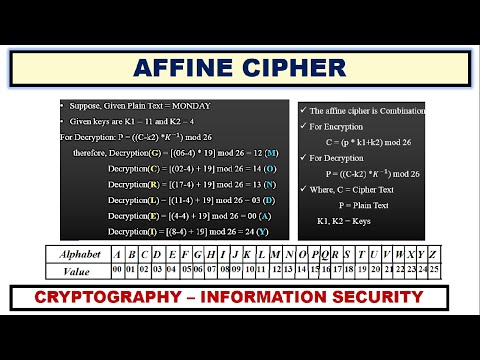
4:23
Affine Cipher Example Cryptanalysis of Monoalphabetic cipher ~xRay Pixy
Ritika xRay Pixy
2.3K views
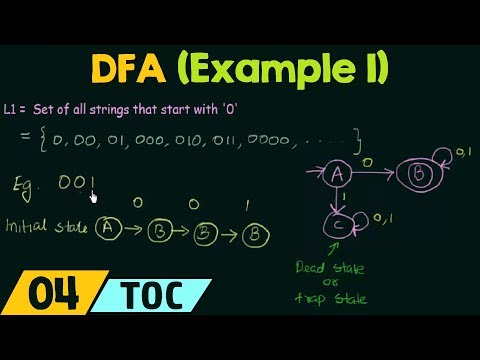
9:48
Deterministic Finite Automata (Example 1)
Neso Academy
2.2M views
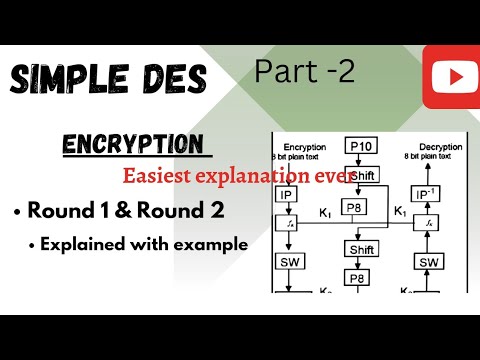
10:40
Encryption of DES with detailed example -Round 1&2- Cryptography | Bs/Ms |2024
Infinite Maths
558 views

14:32
Converting CFG to GNF | Example-1 | TOC | Lec-73 | Bhanu Priya
Education 4u
475.9K views

14:40
Knapsack Algorithm in Cryptography and Network Security with example
Lab Mug
3.8K views

7:05
Non-Deterministic Finite Automata (Solved Example 1)
Neso Academy
965.0K views
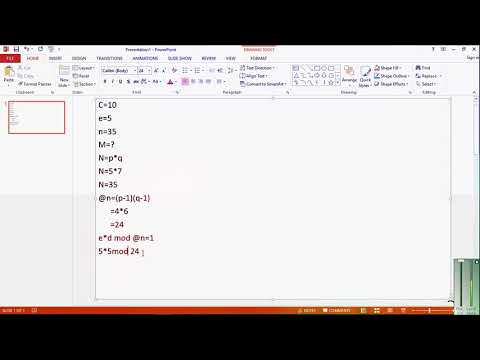
10:54
Rivest, Shamir and Adleman (RSA) hacking example in urdu hindi| complete info about RSA algorithm|46
IT Expert Rai Jazib
75 views

0:34
Write the Mixed Number as a Decimal Example with 5 and 3/10 #shorts
The Math Sorcerer
36.2K views
6:56
Turing Machine for Unary Addition | Easy TM Design with Example | Theory of Computation & Automata
Sagar Choudhary
276 views
3:00
Quick Optimization Example
Andy Math
5.5M views

3:29
How to Record and Edit Your Voice in Audacity | FREE Recording & Editing Software | USB Mic Example
Mike Russell
14.5K views

18:24
RSA ALGORITHM || SECURITY || EXAMPLE || PUBLIC KEY CRYPTOGRAPHY || ASYMMETRIC KEY CRYPTOGRAPHY
t v nagaraju Technical
54.1K views
9:43
Caesar Cipher Explained with Solved Example|lec 3|urdu|hindi
ITphile
379 views
6:39
The ElGamal Algorithm: a simple example
Sunny Classroom
13.6K views
8:40
The RSA Encryption Algorithm (1 of 2: Computing an Example)
Eddie Woo
1.2M views

7:56
What is html in hindi ||bilkul basic se html in hindi || full define html with example | part-1
Corporate Wallah
307 views

15:12
Four Square Cipher - Substitution Cipher with example (Digraph)
Lectures by Shreedarshan K
6.4K views

10:07
Row Transposition Cipher Encryption & Decryption with Example Urdu/Hindi
SLS Tutorials
4.3K views