Search Results for "Secure Transactions"
Find videos related to your search query. Browse through our collection of videos matching "Secure Transactions". Search across titles, descriptions, tags, and channels to discover the content you're looking for.
Search Results for "Secure Transactions"
50 results found

19:03
What is SSL? | What is SSL Ceritificate? | SSL Architecture and Protocols | Secure Socket Layer
Chirag Bhalodia
72.1K views
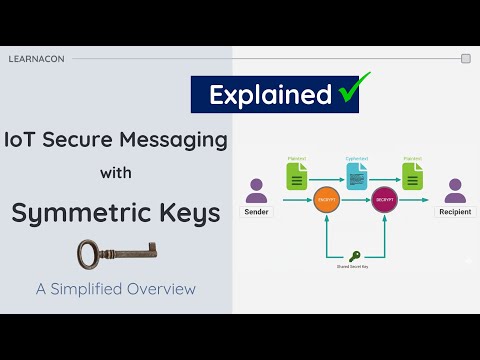
10:05
Secure IoT Messaging with Symmetric Keys: A Simplified Guide
LEARNACON
79 views

5:49
US Marines Still Battling to Secure Fallujah 2004
Channel 4 News
2.2M views

55:35
Cryptography and Network Security Part 4/5 | WIlliam Stallings |Secure communication - S8 EC, CS,KTU
bushara abdulrahim
498 views
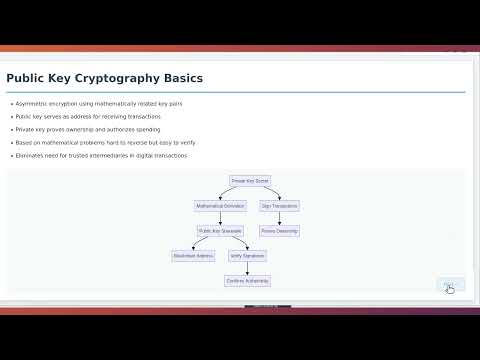
44:23
Blockchain Cryptography Math Explained: A Guide to the Mathematics Behind Secure Digital Ledgers
Network Technician
6 views
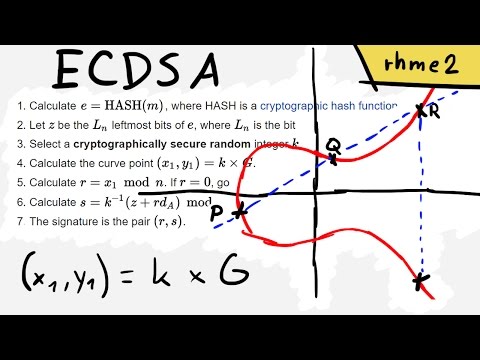
8:19
Breaking ECDSA (Elliptic Curve Cryptography) - rhme2 Secure Filesystem v1.92r1 (crypto 150)
LiveOverflow
78.4K views

28:17
Parte 1 - Introdução ao Algoritmo SHA 256 - Secure Hash Algorithm SHA256
Laboratório de Inutilidade Pública
7.2K views

0:16
Wireless network secure encryption protocol #networksecurity
cyberninja
206 views
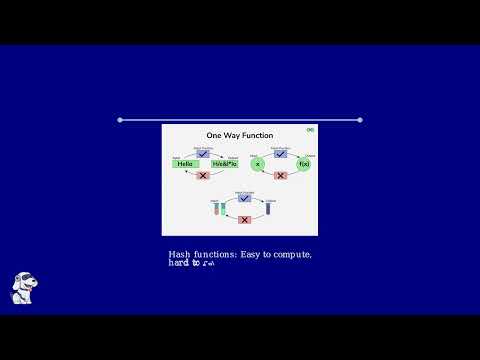
36:07
Quantum Cryptography: How Weird Physics Could Secure Your Secrets Forever
Volkan Duran
55 views

10:22
INFORMATION SECURITY( HINDI).WHAT IS CRYPTOGRAPHY AND HOW IT WORKS TO SECURE YOUR INFORMATION.(ICT)
Computerprime
2.3K views

6:17
Secure QR-Code Based Message Sharing System Using Cryptography and Steganography
SHOAIB SHAIKH
633 views

0:35
Cracking The Code - Exploring Secure Hash Algorithms - SHA Short #cybersecurity #hashing
Technically U
1.1K views

5:31
#54 S/MIME - Secure MIME protocol - Functions, Services |CNS|
Trouble- Free
215.2K views

0:09
Why Sleep Training Might Disrupt Secure Attachment | Gentle Parenting Insights
Shalee Bayne | Wellness & Honest Motherhood
100.1K views

7:41
An RSA-Based Secure Image Steganography Technique Using Adaptive Data Hiding - Mid
Akash Joy
7 views
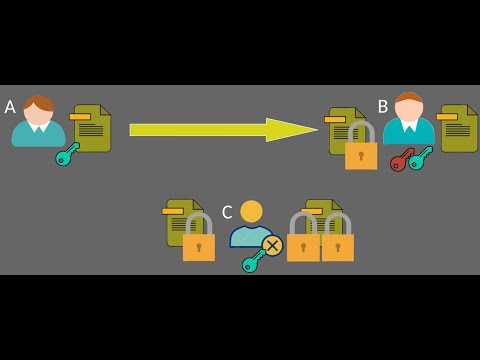
19:53
Understanding Asymmetric Encryption: The Key to Secure Communication
Visualize Byte Code
9 views
12:01
Secure Data Transfer Based on Visual Cryptography - Part1
AmAn
30 views

14:53
Quantum Cryptography: The Future of Secure Communication
CyberSecTV
32 views

0:42
Unlocking the Quantum Internet Future of Secure Communication #quantumInternet #securecommunication
Inspiration Station
11 views

3:59
The Lava Lamps That Help Keep The Internet Secure
Tom Scott
4.2M views
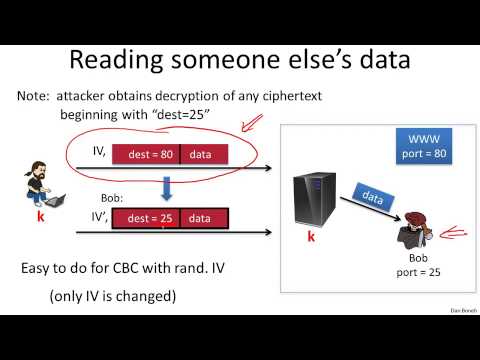
12:54
7 1 Active attacks on CPA secure encryption 13 min
Jake Danniel
305 views
3:17
How Does No-Cloning Theorem Secure Quantum Cryptography? - Quantum Tech Explained
Quantum Tech Explained
0 views

32:28
17-How Public Key Distribution Works? 💡 | Secure Key Sharing in Network Security
Sundeep Saradhi Kanthety
107.5K views

1:02
Techniques for Secure Data Aggregation #ai #artificialintelligence #machinelearning #aiagent
NextGen AI Explorer
6 views
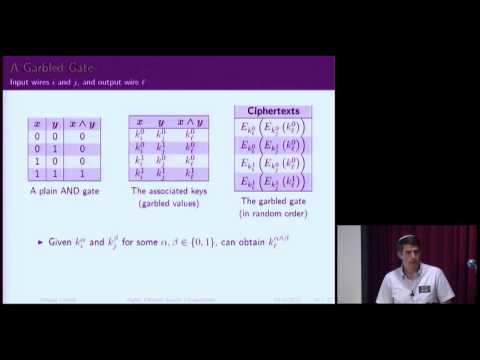
44:45
Yehuda Lindel:Highly Efficient Secure Two-Party Computation - the Road from Theory to Practice
The Open University of Israel
217 views

24:51
Two-Round Multiparty Secure Computation from Minimal Assumptions
IACR
385 views

39:04
Cryptoparty: An Introduction to Secure, Usable Encryption Tools for All
RSA Conference
3.8K views
12:32
Your iPhone Isn’t Secure Enough - 10 Hidden Settings You NEED to Enable
Stephen Robles
139.5K views

2:44
Why Is Quantum Cryptography The Future Of Secure Communication? - Quantum Tech Explained
Quantum Tech Explained
7 views

0:35
Understanding AES Encryption: Simply Explained in 60 Seconds! #ytshorts #secure #internet
Tamilayrus - தமிழ்அய்ரஸ்
785 views

2:17
A Lightweight Image Encryption Algorithm Based on Secure Key Generation
Takeoff Edu Group
229 views

0:27
How Bitcoin Stays Secure - SHA256 & Mining Explained
THE BIT INSIGHT
282 views

2:36
Provably Secure Three-Party Authenticated Quantum Key Distribution Protocols
projectsnine
861 views

30:43
Swift 4: RSA Asymmetric Public Key Encryption - Secure Your iOS 11 App. How to in Xcode 9!
Swift Almanac
7.6K views
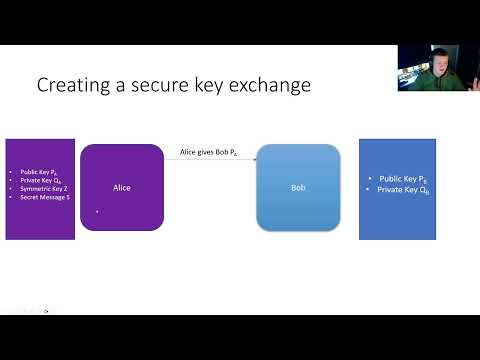
15:54
Cryptography #3 - Asymmetric encryption & a secure key exchange
Ben Folland
28 views
1:33
Secure File Storage in Cloud Computing Using Cryptography in Python | Python Project Ideas
Nevon Projects
56.2K views

5:12
Best 100% FREE VPN in 2025 | No Signup, No Ads, Secure & Safe
PauTECtips
5.5K views

3:22
How to Secure App-Level Encryption Keys with Unbound Key Control (UKC) via REST API
Unbound Security
564 views

7:49
Hybrid Algorithm for secure data over Cloud OS
Avin Pasupuleti
1.4K views

9:49
HAR 2009: How to use quantum cryptography for secure identification 4/6
Christiaan008
151 views

0:15
HOW ! ASUS LAPTOP BOOT MENU BIOS SETTINGS ! SECURE BOOT ! BOOT FROM USB ! DVD ROOM
Vcarelaptops
496.1K views

14:15
Entity Encryption using AES | Spring Boot | JPA | Advanced Encryption Standard | Secure your data
VKS Tech
10.7K views

17:28
10 Principles for Secure by Design: Baking Security into Your Systems
IBM Technology
42.9K views

8:32
Secure Electronic Transaction (SET) in hindi || SET Protocol || Network Security || Akant 360
Unbeaten Learning
63.5K views
![[8B] Forward and Backward-Secure Range-Searchable Symmetric Encryption](/image/i.ytimg.com/vi/3Ri_VXm9SJM/xhqdefault.jpg.pagespeed.ic._ltxPQcbYC.jpg)
12:00
[8B] Forward and Backward-Secure Range-Searchable Symmetric Encryption
Privacy Enhancing Technologies Symposium
244 views

1:04
Java Secure Coding: Data Confidentiality and Integrity 12 2 Asymmetric Crypto
AppSec Labs
823 views

13:45
Secure Binary Image Steganography Using F5 algorithm Based on Data Hiding and Diffusion techniques
Jitendra Singh
954 views
1:09
What is Quantum Secure Communication? All You Need to Know
NewsX Live
276 views

1:02
Unpacking Quantum Cryptography: Will It Secure Our Digital World?
AI BreakDown
1 views

20:10
Saber on ARM: CCA secure module lattice based key encapsulation on ARM
IACR
327 views
Previous Page 2